Docker Runner Fails With Permission Denied Errors in Build Log
Summary
Docker runner fails on Fedora/CentOS/RHEL with SELinux in enforcing mode. Bamboo build fails with a permission denied error in logs because directories mounted from a host to a container are not accessible even for a root container user.
Environment
The issue can be reproduced with any Bamboo version on Fedora/CentOS/RHEL with SELinux running in enforcing mode.
Diagnosis
Build in Docker fails, and you will see the following errors in the job build log:
/tmp/runInDocker8004722310245392322.sh: /home/bamboo/bamboo-agent-home/temp/IPT-BPTD-JOB1-23-ScriptBuildTask-2477866816195297390.sh: Permission deniedIn this particular example, a mounted script with script task syntax cannot be accessed. There can be similar issues with accessing source code in a working directory mounted into a Docker container, for example:
/tmp/runInDocker2036597224817806522.sh: 2: cd: can't cd to /home/bamboo/bamboo-agent-home/xml-data/build-dir/TEST-TES4-JOB1Cause
By default, Docker container processes run with the system_u:system_r:svirt_lxc_net_t:s0 label. The svirt_lxc_net_t type is allowed to read/execute most content under /usr, but it is not allowed to use most other types on the system. As a result, when Bamboo starts a build container and mounts temp and working directories, everything in these directories is not accessible for a user (even if it's root) in the container. This results in exec failures, since mounted files cannot be accessed and thus job tasks cannot be executed.
Solution
There are 4 solutions, ranging from the easiest and less secure to a bit more complicated and secure
Turn off SELinux
Of course, this can be a no-go due to security reasons, however, if turning SELinux off is an option, you can do so, and this will fix the issue.
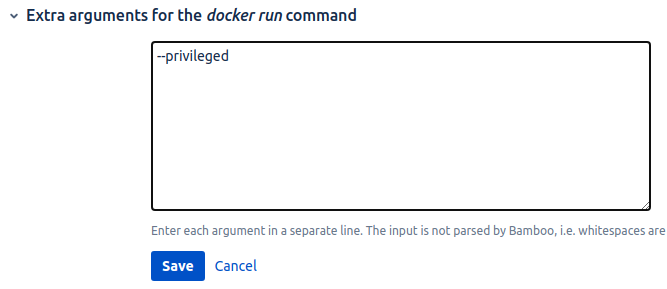
Run container in a privileged mode
This is possible only in 7.1+ versions with the introduction of extra Docker run arguments. Running containers in a privileged mode can also open security risks, so, do it with caution:
Manually add a label to host directory
Attach a proper SELinux policy type label to Bamboo home (xml data or temp, or the entire Bamboo home directory)
chcon -Rt svirt_sandbox_file_t /home/bamboo/bamboo-agent-home/xml-data
chcon -Rt svirt_sandbox_file_t /home/bamboo/bamboo-agent-home/tempAdd :z suffix to volume mount binding
You can also let Docker do the labeling for you by appending :z suffix to a volume mount binding (container directory) in Bamboo UI (Docker configuration for a job).