Clone URL from a Mirror is not available due to CORS policy violations
Platform Notice: Data Center Only - This article only applies to Atlassian products on the Data Center platform.
Note that this KB was created for the Data Center version of the product. Data Center KBs for non-Data-Center-specific features may also work for Server versions of the product, however they have not been tested. Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
Summary
The clone URL from a Bitbucket mirror is not available and does not show up under the dropdown list for repository clone URLs.
Here's a sample clone URL from a mirror:
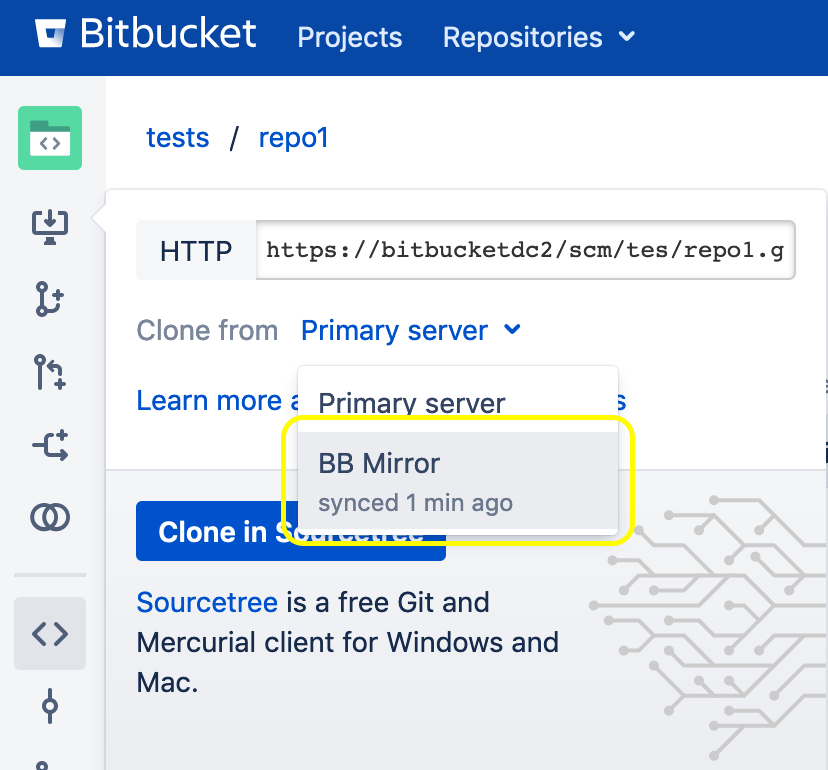
However, in the scenario described in this Knowledge base article, the clone URL is not shown in the dropdown even though there are no issues with the synchronization of projects and repositories from the upstream to the mirror.
The mirror clone URL is not available because the request to load the clone URL is possibly blocked by Cross-Origin Resource Sharing (CORS) security policies at the client-side.
Environment
Bitbucket Data Center with Smart Mirrors or Mirror Farms
Diagnosis
Confirm that there are no issues with synchronization of projects and repositories from the upstream to the mirror by checking the mirror log files for any errors. Please check the links under Troubleshooting Smart Mirroring.
To troubleshoot possible CORS policy violations at the client-side:
Generate a HAR file while loading the clone URLs for a repository
Check the browser's Console logs for any error messages while loading the clone URLs
Sample Case 1: multiple "Access-Control-Allow-Origin" headers
In this specific example, the request was blocked due to CORS security policy because there was more than one "Access-Control-Allow-Origin" header.
HAR file content
The HAR file excerpt shows that there are two "Access-Control-Allow-Origin" headers
1
2
3
4
5
6
7
8
9
10
...
{
"name": "Access-Control-Allow-Origin",
"value": "*"
},
{
"name": "Access-Control-Allow-Origin",
"value": "https://<upstream>"
},
...Browser Console log output
1
Access to XMLHttpRequest at 'https://<mirror>/bitbucket/rest/mirroring/latest/upstreamServers/<upstream-id>/repos/<repo-id>?jwt=<token>' from origin 'https://<upstream>' has been blocked by CORS policy: Response to preflight request doesn't pass access control check: The 'Access-Control-Allow-Origin' header contains multiple values '*, https://<upstream>', but only one is allowed.Cause
The request was blocked due to CORS security policy violations.
Sample Case 1
For this case, the issue was due to misconfiguration in the reverse proxy in front of the mirror where an additional "Access-Control-Allow-Origin: *" was being added by the proxy.
Solution
Resolution
Sample Case 1
Review the reverse proxy configuration and remove the setting that was adding the extra "Access-Control-Allow-Origin: *".
Was this helpful?