Assets Azure Integration Fails with Error AuthorizationFailed
Platform Notice: Data Center Only - This article only applies to Atlassian products on the Data Center platform.
Note that this KB was created for the Data Center version of the product. Data Center KBs for non-Data-Center-specific features may also work for Server versions of the product, however they have not been tested. Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
Summary
After configuring the Assets—Azure Integration, the synchronization of Azure data into Assets fails with an error message.
1
2
2024-08-06 11:03:04,547+0200 http-nio-8081-exec-8 ERROR /rest/insight/1.0/import/module/test/insight-azure-import [c.r.j.p.a.imports.manager.AzureClientProvider] Error validating client.
com.microsoft.azure.CloudException: Status code 403, {"error":{"code":"AuthorizationFailed","message":"The client 'abc' with object id '123' does not have authorization to perform action 'Microsoft.Resources/subscriptions/read' over scope '/subscriptions/abcd' or the scope is invalid. If access was recently granted, please refresh your credentials."}}: Environment
JSM Server/Data Center on any version
Diagnosis
As outlined in the integration document, the process of assigning Application Roles entails directly assigning the reader role to the Access Application. Nevertheless, certain organizations adhere to internal policies that mandate the management of IAM roles through groups.
In these situations, it's advisable to create a group in IAM, then include the Access Application as a member of that group, and lastly, assign the role to the newly formed group.
Cause
The issue stems from assigning an incorrect custom role named read-only to the group. Instead of this custom read-only role, the Reader role should be assigned to the group to which the application belongs.
Solution
For the integration of Azure assets, it is essential to adhere to all the steps outlined in the integration document. Additionally, the following extra steps must be taken into account for assigning roles through groups.
Follow the documentation and create the Access Application.
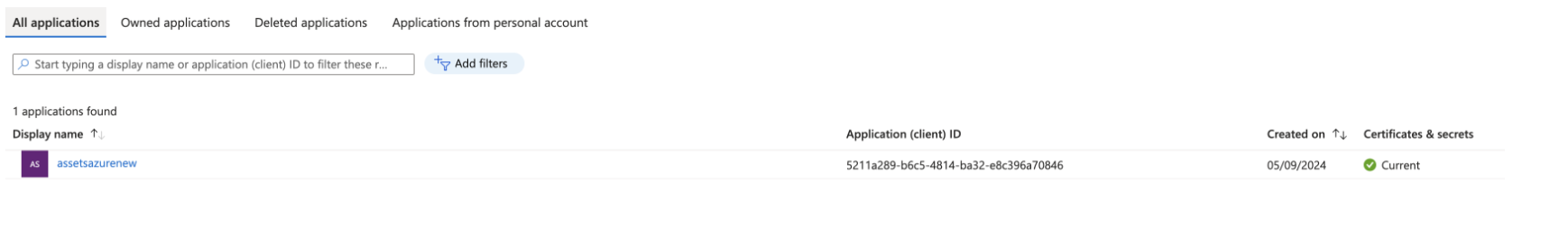
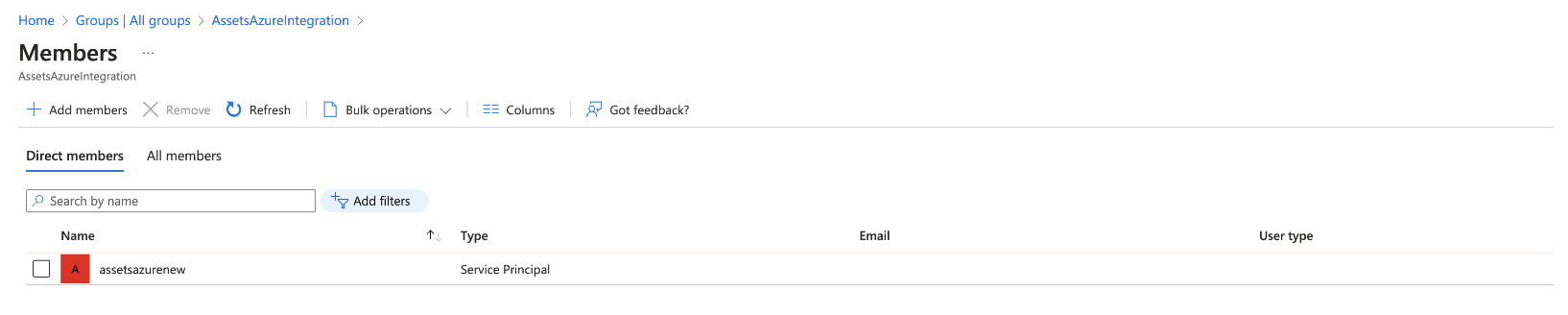
Create a group and add the application created in the previous step as a member. In this example, the group name is AssetsAzureintegration, and the access application is assetsazurenew, which will be included in the group.
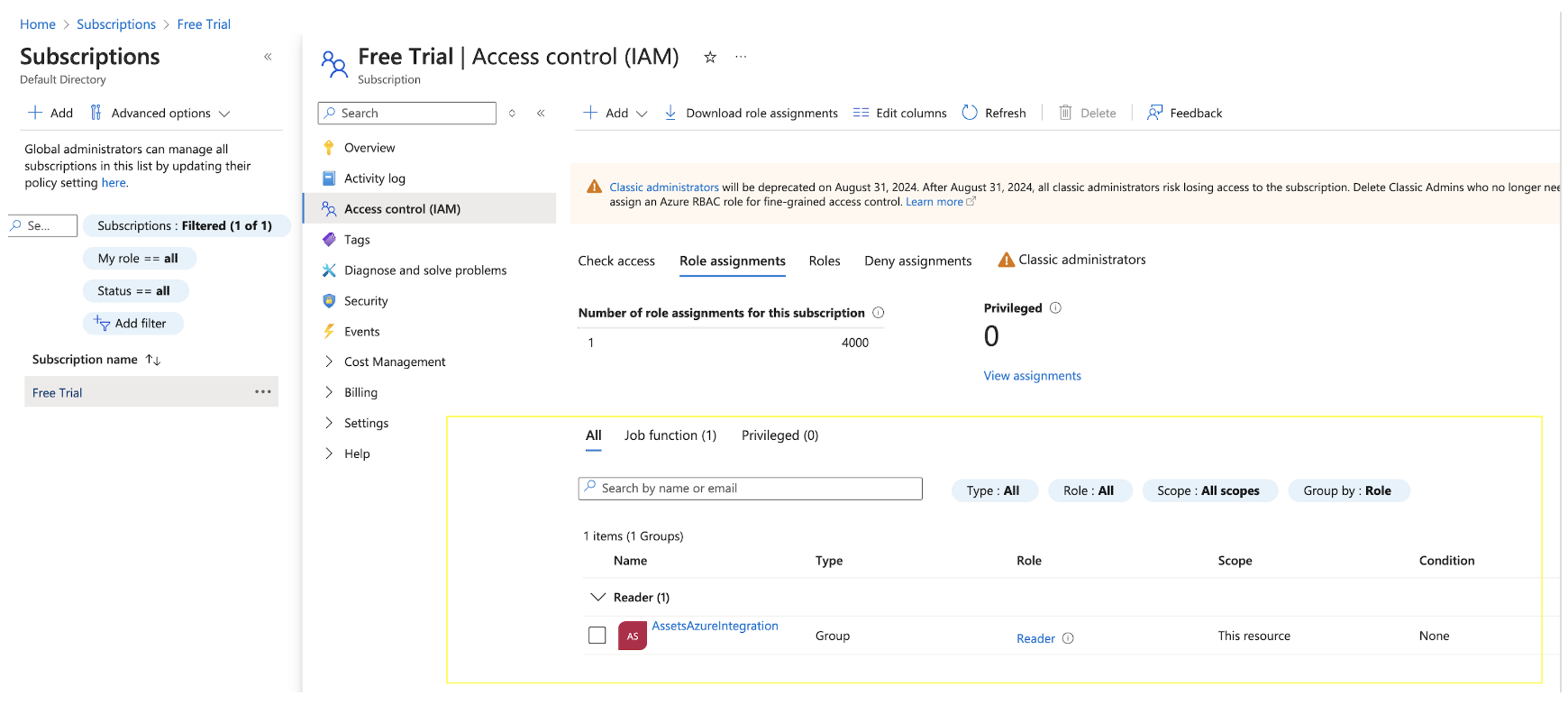
Assign the built-in role called "Reader" to the group created in the previous step.
All the other steps are the same as documented in the integration document.
Was this helpful?