The Jira (or JSM) Mail Handler stops processing new incoming emails due to the error "The provided client secret keys for app XXXXXXXX are expired"
Platform Notice: Data Center - This article applies to Atlassian products on the Data Center platform.
Note that this knowledge base article was created for the Data Center version of the product. Data Center knowledge base articles for non-Data Center-specific features may also work for Server versions of the product, however they have not been tested. Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
Summary
Jira issues are no longer created from incoming emails, when using one of the 2 types of Mail Handlers listed below, configured using OAuth 2.0 integration with Microsoft Azure for authentication as per Detailed steps to configure OAuth 2.0 integration with Microsoft Azure:
- a Jira Mail Handler configured in the page ⚙ > System > Incoming Mail
- a Jira Service Management (JSM) Mail Handler configured in the page Project Settings > Email Requests
In the case of a Jira Mail Handler
When checking on ⚙ > System > Incoming Mail you get an error message about
Unfortunately no connection was possible. Review the errors below and rectify:
Refresh Token Failed. Reported Reason: AADSTS7000222 .....In the case of a JSM Mail Handler
When checking the Audit Logs > Connectivity Log page, the error below can be seen in the UI:
OAuth token not defined for connection. OAuth Authorisation required.Environment
- Jira 8.10.0 or higher, configured with a Jira Mail Handler using the Oauth 2.0 authentication, via ⚙ > System > Incoming Mail
- Or JSM (Jira Service Management) 4.10.0 or higher, configured with a JSM Mail Handler using the Oauth 2.0 authentication, via Project Settings > Email Requests
Diagnosis
In the atlassian-jira.log file entries like the following can be found:
2023-09-06 10:32:29,935-0700 Caesium-1-1 WARN ServiceRunner [c.a.j.i.m.p.feature.oauth.MailOAuthServiceImpl] Recoverable exception fetching OAuth token com.atlassian.oauth2.client.api.storage.token.exception.RecoverableTokenException: An error has occurred while refreshing OAuth token at com.atlassian.oauth2.client.storage.DefaultTokenHandler.handleFailure(DefaultTokenHandler.java:170) at com.atlassian.oauth2.client.storage.DefaultTokenHandler.refreshToken(DefaultTokenHandler.java:156) Caused by: com.atlassian.oauth2.client.api.lib.token.TokenServiceException: AADSTS7000222: The provided client secret keys for app 'xxxxxxxxxxx' are expired. Visit the Azure portal to create new keys for your app: https://aka.ms/NewClientSecret, or consider using certificate credentials for added security: https://aka.ms/certCreds. Trace ID: xxxxxxxxxx Correlation ID: xxxxxxxxxxx Timestamp: 2023-09-06 17:32:29Z at com.atlassian.oauth2.client.lib.token.DefaultTokenService.getToken(DefaultTokenService.java:146)And/Or the following in the atlassian-jira-incoming-mail.log file:
2024-03-08 23:03:23,128-0600 ERROR [xxxxxxx] Caesium-1-3 anonymous xxxxxxx: The folder has been closed on us, stop processing any more emails: * BYE Session invalidated - AccessTokenExpired javax.mail.FolderClosedException: * BYE Session invalidated - AccessTokenExpired at com.sun.mail.imap.IMAPMessage.loadFlags(IMAPMessage.java:1609) [jakarta.mail-1.6.5-atlassian-2.jar:1.6.5-atlassian-2] at com.sun.mail.imap.IMAPMessage.isSet(IMAPMessage.java:1072) [jakarta.mail-1.6.5-atlassian-2.jar:1.6.5-atlassian-2]And/Or the following in the atlassian-jira-incoming-mail.log file:
2024-08-19 22:54:16,570-0600 Caesium-1-1 WARN ServiceRunner [c.a.j.i.m.p.feature.oauth.MailOAuthServiceImpl] Recoverable exception fetching OAuth token com.atlassian.oauth2.client.api.storage.token.exception.RecoverableTokenException: An error has occurred while refreshing OAuth token at com.atlassian.oauth2.client.storage.DefaultTokenHandler.handleFailure(DefaultTokenHandler.java:170) at com.atlassian.oauth2.client.storage.DefaultTokenHandler.refreshToken(DefaultTokenHandler.java:156) at com.atlassian.oauth2.client.storage.DefaultTokenHandler.refreshTokenIfNeeded(DefaultTokenHandler.java:131) at com.atlassian.oauth2.client.storage.DefaultTokenHandler.lambda$getRefreshedToken$1(DefaultTokenHandler.java:110) at com.atlassian.oauth2.common.concurrent.KeyedLocks.executeWithLock(KeyedLocks.java:37) at com.atlassian.oauth2.client.storage.DefaultTokenHandler.getRefreshedToken(DefaultTokenHandler.java:109) at com.atlassian.oauth2.client.storage.DefaultTokenHandler.getRefreshedToken(DefaultTokenHandler.java:102) at com.atlassian.oauth2.client.storage.DefaultTokenHandler.getRefreshedToken(DefaultTokenHandler.java:35) at jdk.internal.reflect.GeneratedMethodAccessor2619.invoke(Unknown Source) at java.base/jdk.internal.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) at java.base/java.lang.reflect.Method.invoke(Method.java:566) at org.springframework.aop.support.AopUtils.invokeJoinpointUsingReflection(AopUtils.java:344) at org.eclipse.gemini.blueprint.service.importer.support.internal.aop.ServiceInvoker.doInvoke(ServiceInvoker.java:56) at org.eclipse.gemini.blueprint.service.importer.support.internal.aop.ServiceInvoker.invoke(ServiceInvoker.java:60) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) at org.springframework.aop.support.DelegatingIntroductionInterceptor.doProceed(DelegatingIntroductionInterceptor.java:137) at org.springframework.aop.support.DelegatingIntroductionInterceptor.invoke(DelegatingIntroductionInterceptor.java:124) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) at org.eclipse.gemini.blueprint.service.util.internal.aop.ServiceTCCLInterceptor.invokeUnprivileged(ServiceTCCLInterceptor.java:70) at org.eclipse.gemini.blueprint.service.util.internal.aop.ServiceTCCLInterceptor.invoke(ServiceTCCLInterceptor.java:53) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) at org.eclipse.gemini.blueprint.service.importer.support.LocalBundleContextAdvice.invoke(LocalBundleContextAdvice.java:57) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) at org.springframework.aop.support.DelegatingIntroductionInterceptor.doProceed(DelegatingIntroductionInterceptor.java:137) at org.springframework.aop.support.DelegatingIntroductionInterceptor.invoke(DelegatingIntroductionInterceptor.java:124) at org.springframework.aop.framework.ReflectiveMethodInvocation.proceed(ReflectiveMethodInvocation.java:186) at org.springframework.aop.framework.JdkDynamicAopProxy.invoke(JdkDynamicAopProxy.java:241) at com.sun.proxy.$Proxy1795.getRefreshedToken(Unknown Source) at com.atlassian.jira.internal.mail.processor.feature.oauth.MailOAuthServiceImpl.getOAuthToken(MailOAuthServiceImpl.java:53) at com.atlassian.jira.internal.mail.processor.feature.authentication.OAuthAuthenticationStrategy.getPassword(OAuthAuthenticationStrategy.java:31) at com.atlassian.jira.internal.mail.processor.feature.puller.MailPullerWorker.getMailServerPassword(MailPullerWorker.java:255) at com.atlassian.jira.internal.mail.processor.feature.puller.MailPullerWorker.pullEmailForConnection(MailPullerWorker.java:140) at com.atlassian.jira.internal.mail.processor.feature.puller.MailPullerWorker.pullMailFromAllValidChannels(MailPullerWorker.java:100) at com.atlassian.jira.internal.mail.processor.feature.puller.MailPullerService.run(MailPullerService.java:33) at com.atlassian.jira.internal.mail.processor.services.MailPullerExecutor.run(MailPullerExecutor.java:29) at com.atlassian.jira.internal.mail.processor.services.AbstractMailExecutor.execute(AbstractMailExecutor.java:45) at com.atlassian.jira.internal.mail.processor.services.MailJobRunner.runJob(MailJobRunner.java:35) at com.atlassian.scheduler.core.JobLauncher.runJob(JobLauncher.java:134) at com.atlassian.scheduler.core.JobLauncher.launchAndBuildResponse(JobLauncher.java:106) at com.atlassian.scheduler.core.JobLauncher.launch(JobLauncher.java:90) at com.atlassian.scheduler.caesium.impl.CaesiumSchedulerService.launchJob(CaesiumSchedulerService.java:435) at com.atlassian.scheduler.caesium.impl.CaesiumSchedulerService.executeClusteredJob(CaesiumSchedulerService.java:430) at com.atlassian.scheduler.caesium.impl.CaesiumSchedulerService.executeClusteredJobWithRecoveryGuard(CaesiumSchedulerService.java:454) at com.atlassian.scheduler.caesium.impl.CaesiumSchedulerService.executeQueuedJob(CaesiumSchedulerService.java:382) at com.atlassian.scheduler.caesium.impl.SchedulerQueueWorker.executeJob(SchedulerQueueWorker.java:66) at com.atlassian.scheduler.caesium.impl.SchedulerQueueWorker.executeNextJob(SchedulerQueueWorker.java:60) at com.atlassian.scheduler.caesium.impl.SchedulerQueueWorker.run(SchedulerQueueWorker.java:35) at java.base/java.lang.Thread.run(Thread.java:829) Caused by: com.atlassian.oauth2.client.api.lib.token.TokenServiceException: AADSTS7000222: The provided client secret keys for app 'XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXX' are expired. Visit the Azure portal to create new keys for your app: https://aka.ms/NewClientSecret, or consider using certificate credentials for added security: https://aka.ms/certCreds. Trace ID: 09ddcb73-9a3b-4440-8d11-74862b588f00 Correlation ID: 7ed16942-749f-4fd7-aed7-2cb122e6d1e6 Timestamp: 2024-08-20 04:54:16Z at com.atlassian.oauth2.client.lib.token.DefaultTokenService.getToken(DefaultTokenService.java:150) at com.atlassian.oauth2.client.lib.token.DefaultTokenService.forceRefresh(DefaultTokenService.java:75) at com.atlassian.oauth2.client.storage.DefaultTokenHandler.refreshToken(DefaultTokenHandler.java:144) ... 46 more
Cause
This error indicates that the client secret that was entered in Jira during the setup of the Oauth 2.0 configuration (step 22 of Detailed steps to configure OAuth 2.0 integration with Microsoft Azure) is no longer valid.
You will need to update these expired secrets for this Oauth 2.0 application link.
Solution
Renew the client secret using the following steps:
- In Azure
- Go to https://portal.azure.com/
- Click on App registrations
- Search for the application
- Under the Manage section, click on Certificates & Secrets
- Under client secrets, click on + New client secret
- Choose a description and expiration date
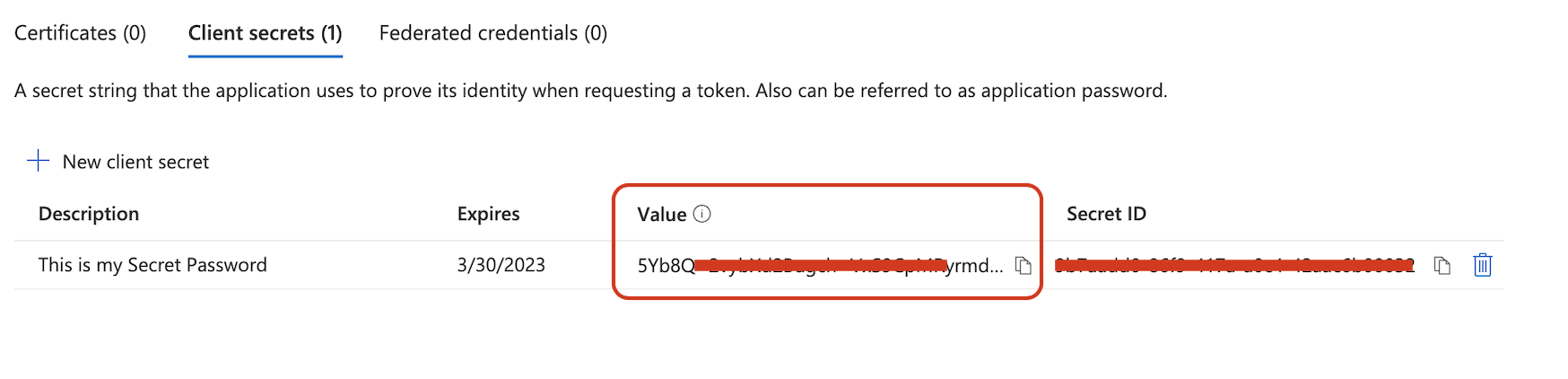
Take note of the Value generated, this "Value" will be used as the "Client secret" at Jira.
Known errors:
The "Value" is the "Client secret" we need to use on Jira.
The "Secret ID" is not the password and will cause an authentication error.
- In Jira
- Go to ⚙ > Applications > Application links
- Edit the Oauth 2.0 application link used by the mail handler to contain the new client secret
- Click on save
- Test the connection