Branch permissions
Branch permissions help enforce specific workflows and prevent errors like a new workspace member deleting master.
With branch permissions you can:
- Closely control which users or groups can write or merge to any branch.
- Create permissions for a specific branch type, or pattern. For example:
/PROJECT-*to limit access to all branches with names likePROJECT-1234.
If you want even tighter control over your workspace's workflow, check out merge checks. Merge checks allow you to recommend or require specific conditions on merges for individual branches or branch patterns. Learn more about merge checks.
Merge checks are a Premium feature for Bitbucket Cloud. Learn more about Bitbucket Premium.
Example permissions set up
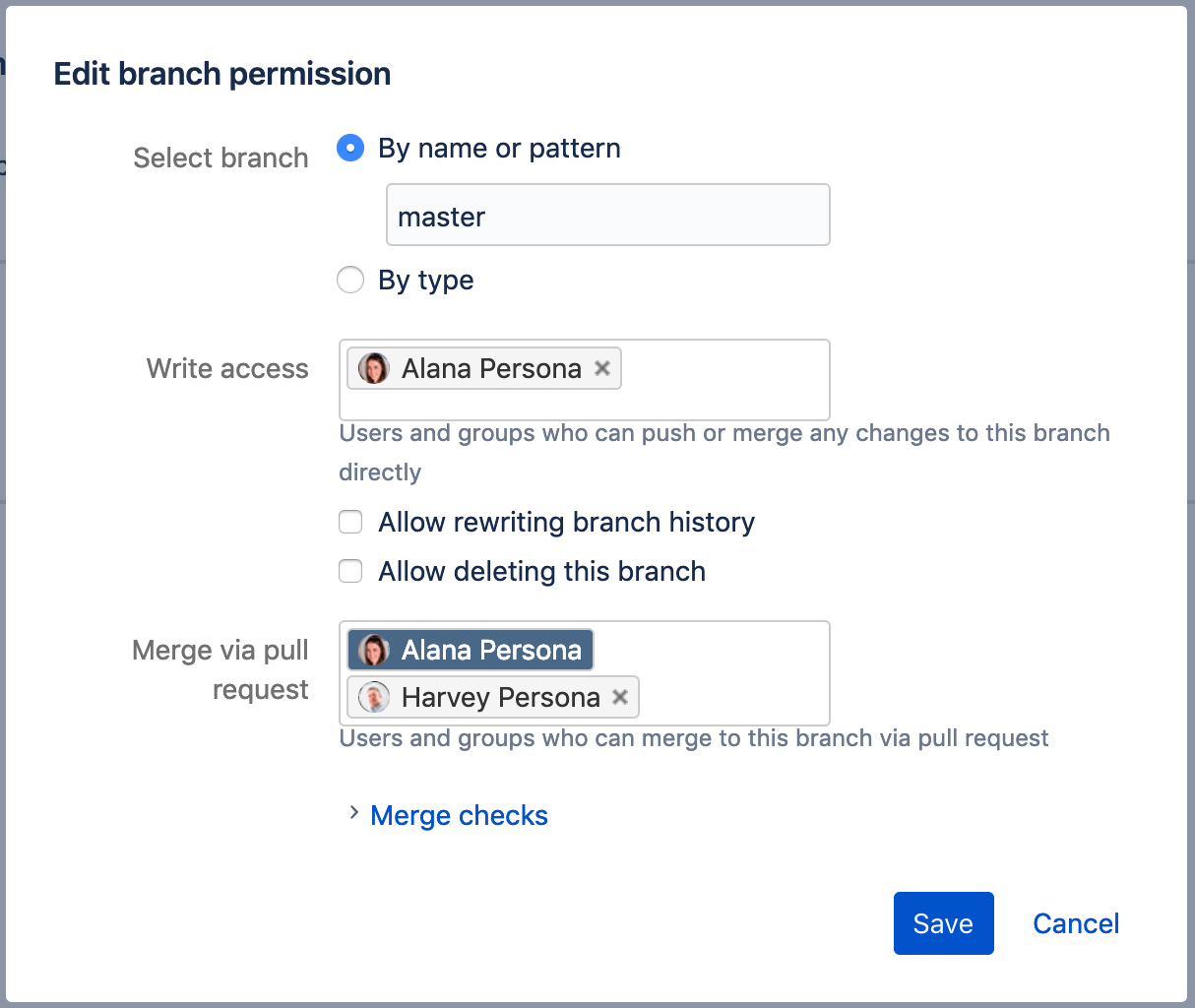
So, let's say Alana (Principal Engineer), Harvey (QA lead), and another 5 engineers are working on a Teams in Space project. You want everyone to be able to do work effectively so everyone has write access to the repository. Now you need to manage access to the repositories master and develop branches. You might want to assign permissions like this:
- Allow only Alana to write directly to master.
- Allow only Alana and Harvey to merge into master.
- Allow everyone to merge to develop but only through a pull request.
Branch types
If you've got the branching model enabled, you can configure permissions for all branches of a specific type. This might be useful if you want to restrict merge access on all release branches, for example.
Branch patterns
If you need to get more granular than type, you can also set permissions for a specific pattern of branch name like PROJECT- by adding a wild card character (*) to either end of the string. For example:
PROJECT-* Matches branch named PROJECT-*, even in a name space, so restrictions would apply to the following branches:
PROJECT-1234
PROJECT-new
PROJECT-1.1
Branch permissions overlap
It's possible to accidentally overlap your branch permissions. For example, if you created a branch permission specifically for the branch name master but also created a permission using the branch pattern *, then, for the master branch, both permissions would be applied.
This table shows examples of results of overlapping permission definitions:
| Wildcard (*) branch patterns | Specific ("master") branch name | What's enforced for branches included in both restrictions |
|---|---|---|
| User or group restrictions (write or merge access) | ||
| No users or groups listed | Alana | Only Alana has access |
| Everybody | Alana | Only Alana has access |
| Alana | Harvey | Both Alana and Harvey have access |
| Alana | No users or groups | Only Alana has access |
| Alana | Everybody | Only Alana has access |