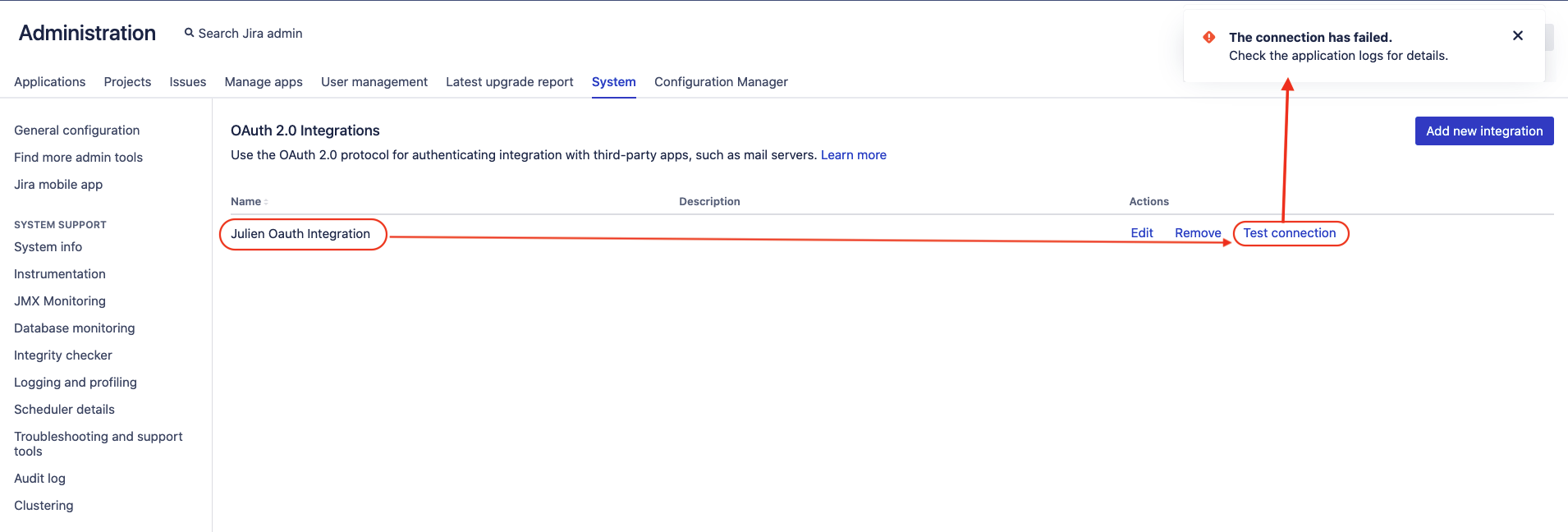
The connection test of the OAuth 2.0 integration fails with the error "The connection has failed. Check the application logs for details."
Platform notice: Server and Data Center only. This article only applies to Atlassian products on the Server and Data Center platforms.
Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
Summary
After configuring an OAuth 2.0 integration in ⚙ > System > OAuth 2.0, when clicking on the Test connection button, the error "The connection has failed. Check the application logs for details." is thrown in the UI:
Environment
Jira 8.10.0 or higher, integrated with a Microsoft Office 365 or Microsoft Exchange mailbox.
Causes
Root Cause 1
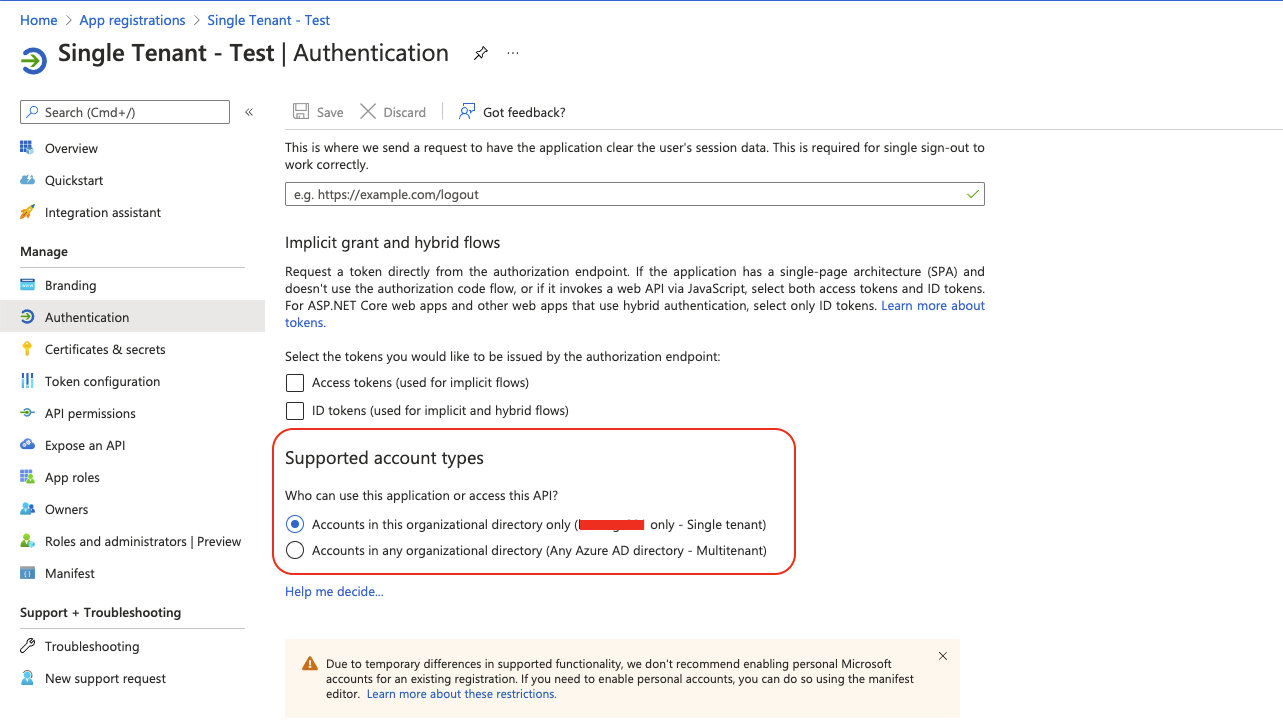
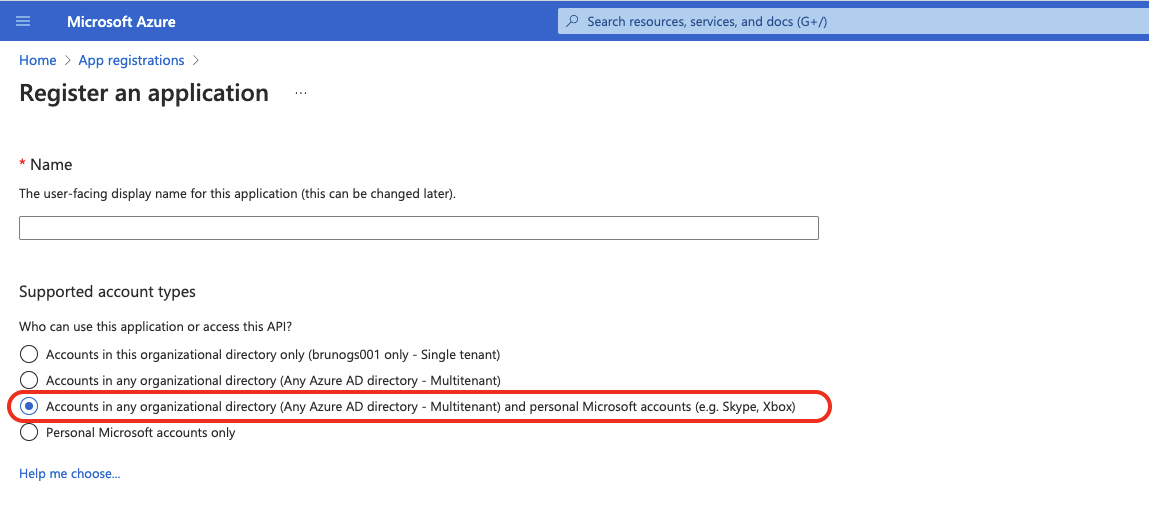
When configuring an OAuth 2.0 integration with the default values provided by Jira for the 2 fields Authorization endpoint and Token endpoint, we recommend using the support account type of the application needs to be set to Accounts in any organizational directory (Any Azure AD directory - Multitenant) and personal Microsoft accounts (e.g. Skype, Xbox).
If the support account type is set to "single-tenant", then the connection test will fail with the default values for the field Authorization endpoint and Token endpoint.
If your organization only allows the "single-tenant" support account type, then it will be necessary to change the 2 fields Authorization endpoint and Token endpoint in the OAuth 2.0 configuration page. Please refer to the section Solution for Root Cause 1.
Root Cause 2
An incorrect Client ID or Client Secret value was used in the OAuth 2.0 configuration.
As explained in the Atlassian community discussion Why can't I connect to Microsoft with oAuth2.0 setup?, when using Microsoft Exchange (or Office 365):
- the Client ID field should be set to the Application (client) ID from application created in the Azure portal
- the Client Server field should be set to the value generated when clicking on the New client secret button from the application created in the Azure portal
Root Cause 3
If Jira is configured to use Java 8u121 version, then the problem might be caused by recent changes in Java 8u111.
According to the 8u111 release notes:
Disable Basic authentication for HTTPS tunneling:
In some environments, certain authentication schemes may be undesirable when proxying HTTPS. Accordingly, the Basic authentication scheme has been deactivated, by default, in the Oracle Java Runtime .. Now, proxies requiring Basic authentication when setting up a tunnel for HTTPS will no longer succeed by default. If required, this authentication scheme can be reactivated by removing Basic from the jdk.http.auth.tunneling.disabledSchemes networking property, or by setting a system property of the same name to "" ( empty ) on the command line.
Root Cause 4
There is some Firewall Egress Filtering which is incorrectly configured and which is blocking the OAuth traffic.
Root Cause 5
The user who logged into the Microsoft Portal while testing the Oauth 2.0 integration does not have the permission to authorize this integration, and the right permission needs to be configured on the Microsoft/Azure side.
It is worth noting that:
- the Oauth 2.0 integration implemented in Jira only supports the OAuth 2.0 authorization code flow
- the OAuth 2.0 client credentials flow is currently not supported, which is the reason why the Jira admin user is always redirected to the Microsoft Login page when testing the Oauth 2.0 connection, since this integration needs to be authorized through the Microsoft UI
- There is an open feature request dedicated to implement the client credentials flow, which is tracked in OAUTH20-176 - Client Credential Grant Flow for OAuth 2.0
Root Cause 6
The URL used when creating the applink is incorrect
Root Cause 7
A incorrect set of scopes (mixing different domains) is used in the Oauth 2.0 configuration.
An example of incorrect set of scopes is shown below:
https://outlook.office.com/IMAP.AccessAsUser.All
https://outlook.office365.com/POP.AccessAsUser.All We can see in this combination of scopes that one of them is using outlook.office.com (which is meant for non-GCC accounts), and the other one is using outlook.office365.com. When testing the connection for the Oauth 2.0 configuration, Microsoft will return with an error complaining about these scopes because they contain "more than one resource", and the connection test will fail.
Root Cause 8
An SSL certificate is missing in the Java Truststore used by the Jira application, which prevents Jira from being able to send requests to the Microsoft (or Google) Authorization and Token endpoints in order to get an Oauth token.
Diagnosis
Diagnosis for Root Cause 1
If you find the following error the Jira application logs, then the Root cause 1 is relevant:
2021-11-16 12:35:50,956+0100 https-jsse-nio-8443-exec-7 ERROR julien 755x4397x2 lyskqh 127.0.0.1 /rest/oauth2-client/latest/config/flow/d4ec2ed5-fa07-4e3d-948d-0ce99fb20a40 [c.a.o.c.rest.resource.ClientConfigurationResource] Error occurred while authorizing an integration. The error message is: Error when fetching authorization response: {"error_description":"AADSTS50194: Application '79c86cf8-e761-4fdc-bc20-a629c5d04260'(Single Tenant - Test) is not configured as a multi-tenant application. Usage of the \/common endpoint is not supported for such applications created after '10\/15\/2018'. Use a tenant-specific endpoint or configure the application to be multi-tenant.\r\nTrace ID: d7599cf0-813f-4495-8317-577479857f00\r\nCorrelation ID: 34687097-cd9a-4300-9639-b561f5effd26\r\nTimestamp: 2021-11-16 11:35:47Z", "error":"invalid_request"}- Log into the Azure portal (https://portal.azure.com/), go to App Registration > Select application > Authentication, and check the Supported Account Types setting. If it is set to Accounts in this organizational directory only (XXXXXX only - Single tenant), then Root cause 1 is relevant:
Diagnosis for Root Cause 2
Check the Jira application logs. If you find either of the errors below, then the Root Cause 2 is relevant:
Example 1:
2021-09-13 09:02:13,597+0000 http-nio-8080-exec-7 ERROR dragan 542x294x1 4eic3i 10.132.134.112,127.0.0.1 /rest/oauth2-client/latest/config/flow/b637a37a-80d4-4407-8847-0b0726c3ac63 [c.a.o.c.rest.resource.ClientConfigurationResource] Error occurred while authorizing an integration. The error message is: AADSTS7000215: Invalid client secret is provided. Trace ID: 15582ef9-f50c-49d2-bbea-ed98debc4d00 Correlation ID: b56ef91f-c6af-4026-8226-7ec6ed7e5589 Timestamp: 2021-09-13 09:02:12ZExample 2:
2021-02-04 17:17:20,673+0000 http-nio-8080-exec-214 url: /rest/oauth2-client/latest/config/flow/a5c88fb2-8edc-4f6c-b496-190405222009; user: testuser ERROR testuser 1037x178772x2 1vgh9dz XX.XX.XXX.XX /rest/oauth2-client/latest/config/flow/XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX [c.a.o.c.rest.resource.ClientConfigurationResource] Error occurred while authorizing an integration. The error message is: AADSTS7000215: Invalid client secret provided. Ensure the secret being sent in the request is the client secret value, not the client secret ID, for a secret added to app 'XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXX'. Trace ID: a5bbfead-d47d-4da5-8ad6-f097ed7e8b00 Correlation ID: 6f0462af-0baa-40ce-b62d-0723e5e7f2a8 Timestamp: 2021-02-04 17:17:16Z
Diagnosis for Root cause 3
If Jira is configured with an outbound proxy, and if you see the following error in the Jira application logs, then Root cause 3 is relevant:
2021-06-22 09:35:52,938+0200 ajp-nio-0.0.0.0-8029-exec-6 ERROR NPUEMA 575x5172383x2 1jg282h 10.146.17.33
/rest/oauth2-client/latest/config/flow/dd20be92-0b16-4692-a587-a0dceb4d1095 [c.a.o.c.rest.resource.ClientConfigurationResource]
Error occurred while authorizing an integration. The error message is:
java.io.IOException: Unable to tunnel through proxy. Proxy returns "HTTP/1.1 407 Proxy Authentication Required"Diagnosis for Root Cause 4
If you find one of the following errors in the Jira application logs, then the Root cause 4 might be relevant:
- Example 1:
2021-12-09 12:48:21,943-0500 http-nio-8080-exec-18 ERROR jirauser XXXxXXXXxX XXXXX XX.XXX.XX.XXX,XX.XXX.XX.XXX
/rest/oauth2-client/latest/config/flow/XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXX [c.a.o.c.rest.resource.ClientConfigurationResource]
Error occurred while authorizing an integration. The error message is:
java.net.ConnectException: Connection timed out (Connection timed out)- Example 2:
2022-03-20 08:30:01,778-0700 https-jsse-nio-8443-exec-6 ERROR jirauser XXXxXXXXxX XXXXX XX.XXX.XX.XXX,XX.XXX.XX.XXX
/rest/oauth2-client/latest/config/flow/XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXX [c.a.o.c.rest.resource.ClientConfigurationResource]
Error occurred while authorizing an integration. The error message is:
javax.net.ssl.SSLException: Connection resetDiagnosis for Root Cause 5
If you see the following error coming from Microsoft after logging into the Microsoft portal (and after clicking on the Oauth 2.0 Test Connection button), then the Root Cause 5 is relevant:
needs permission to access resources in your organization that only an admin can grant. Pease ask an admin to grant permission to this app before you can use it Diagnosis for Root Cause 6
If you find the following type of error in the atlassian-jira.log, it means there's an issue with trying to access the URL in the applink:
2022-05-09 19:35:20,069+0000 http-nio-8080-exec-275 ERROR dbuswell 1175x3644045x1 ldr2th 71.198.159.0,10.0.3.27,0:0:0:0:0:0:0:1 /rest/oauth2-client/latest/config/flow/4fbada08-3c12-40ca-8083-17f5175a28b3 [c.a.o.c.rest.resource.ClientConfigurationResource] Error occurred while authorizing an integration. The error message is: Error when fetching authorization response: {"error_description":"AADSTS500011: The resource principal named https:\/\/graph.micrsoft.com was not found in the tenant named 67b039ac-f578-42c6-9b5b-aa1b5bb0388f. This can happen if the application has not been installed by the administrator of the tenant or consented to by any user in the tenant. You might have sent your authentication request to the wrong tenant.Diagnosis for Root Cause 7
If you find the following type of error in the file atlassian-jira.log, it means that there is a combination of scopes using different domains (in this example https://outlook.office.com/IMAP.AccessAsUser.All https://outlook.office365.com/POP.AccessAsUser.All), and this root cause is relevant:
2022-10-10 12:05:41,545+0000 http-nio-8080-exec-4 ERROR admin 725x157x1 XXXXXXX XXX.XX.XX.XX,XX.XX.X.X /rest/oauth2-client/latest/config/flow/67513c3d-f6a4-4f93-ab37-f1bd822e68c9 [c.a.o.c.rest.resource.ClientConfigurationResource] Error occurred while authorizing an integration. The error message is: AADSTS28000: Provided value for the input parameter scope is not valid because it contains more than one resource. Scope https://outlook.office.com/IMAP.AccessAsUser.All https://outlook.office365.com/POP.AccessAsUser.All offline_access is not valid.
Trace ID: e32c07cf-b6b5-46e0-a570-00f7bd524700
Correlation ID: f42c3c1f-7755-4154-a793-859caf0e3565
Timestamp: 2022-10-10 12:05:40Z
Diagnosis for Root Cause 8
If you find the following type of error in the file atlassian-jira.log, it means that an SSL certificate is missing in the Java Truststore used by the Jira application, and this root cause is relevant:
2022-11-23 12:44:47,310+0000 ajp-nio-127.0.0.1-8009-exec-10 ERROR admin 764x277853x2 XXXXXXX XXX.XX.XX.XX,XX.XX.X.X /rest/oauth2-client/latest/config/flow/5174c727-52c0-4f2a-96b5-d0ca61a1ccd2 [c.a.o.c.rest.resource.ClientConfigurationResource] Error occurred while authorizing an integration. The error message is: javax.net.ssl.SSLHandshakeException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested targetSolution
Solution for Root Cause 1
If your organization allows the "multi-tenant" support account type
Go to the Azure Admin UI, and either edit the current application, so that the supported account type is set to "multitenant", or create a new application by making sure to select the type Accounts in any organizational directory (Any Azure AD directory - Multitenant) and personal Microsoft accounts (e.g. Skype, Xbox):
If your organization only allows the "single-tenant" support account type
Follow the steps below:
- In the Azure Admin UI, get the tenant ID value, as explained in OAuth 2.0 and OpenID Connect protocols on the Microsoft identity platform, and as illustrated in the screenshot below:
- In Jira, go to ⚙ > System > OAuth 2.0, and change the 2 fields Authorization endpoint and Token endpoint in the OAuth 2.0 configuration page, using the following values instead (please replace <TENANT_ID> with the tenant ID):
- Authorization endpoint: https://login.microsoftonline.com/<TENANT_ID>/oauth2/v2.0/authorize
- Token endpoint: https://login.microsoftonline.com/<TENANT_ID>/oauth2/v2.0/token
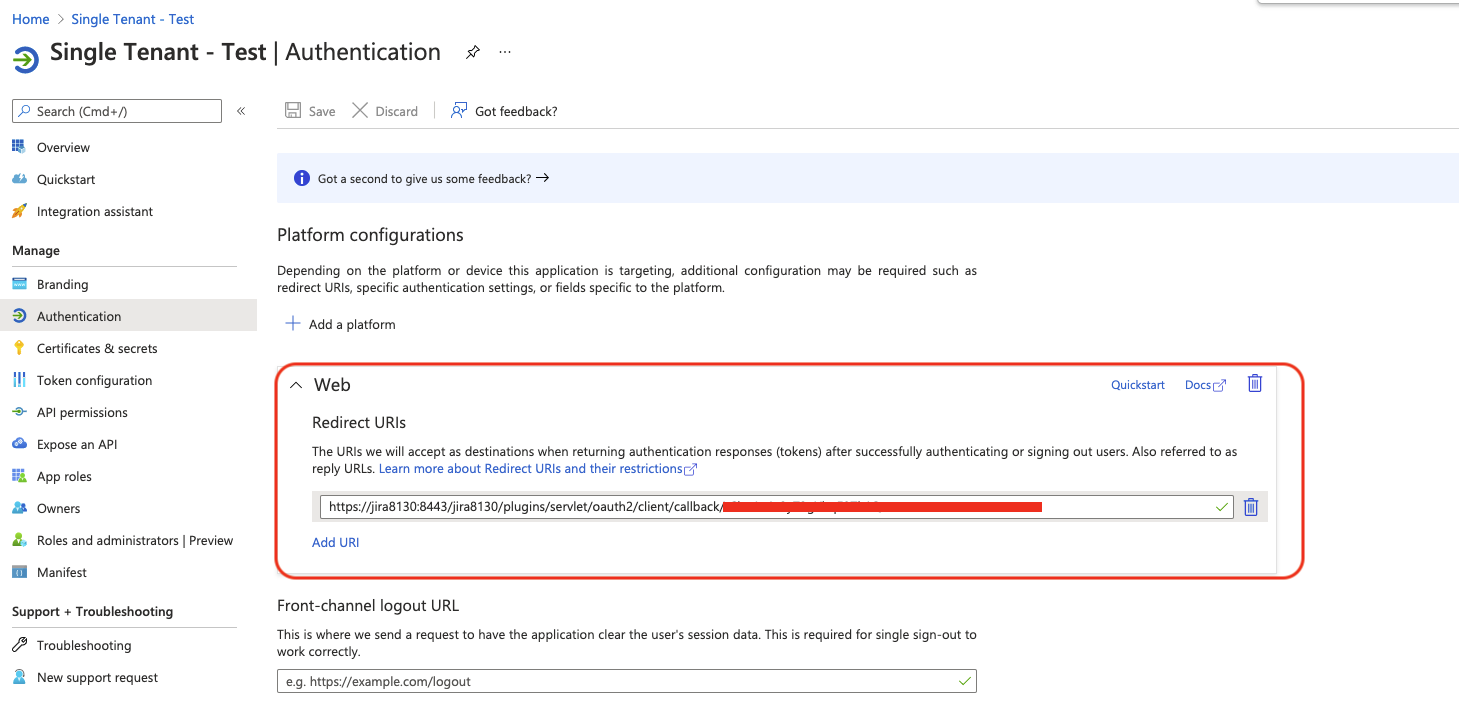
- After you make these 2 changes, make sure to generate a new value for the Redirect URL field, in order to save the new integration settings
- Go back to the Azure Admin UI, update the new Redirect URL value in the application in Authorization > Platform Configurations > Redirect URIs and save the changes:
Solution for Root Cause 2
Configure the Client Id and the Client Secret values as explained in Why can't I connect to Microsoft with oAuth2.0 setup?
Solution for Root Cause 3
Add the following flag to the JVM startup parameters, and re-start the Jira application:
-Djdk.http.auth.tunneling.disabledSchemes=Solution for Root Cause 4
Engage your Firewall administrator to fix the configuration of the Firewall filtering to allow the OAuth traffic. For instance, make sure traffic between Jira and the following URLs is allowed:
- for Microsoft Office 365: outlook.office365.com, login.microsoftonline.com
- for Google: mail.google.com, accounts.google.com
Solution for Root Cause 5
Ensure that the user who logged into the Microsoft Portal while testing the Oauth 2.0 integration has the right permission to authorize this integration. For assistance on this matter, please reach out to your Azure administrator.
Solution for Root Cause 6
In the example code segment from the Diagnosis section for this, you can see that the URL listed in the error is misspelled:"The resource principal named https:\/\/graph.micrsoft.com was not found in the tenant named ...". You will want to update the URL in the applink to the correct one and reattempt the integration.
Solution for Root Cause 7
Make sure that all the scopes used in the Oauth 2.0 configuration on the Jira side as using the same domain.
For example:
this is an incorrect set of scopes
https://outlook.office.com/IMAP.AccessAsUser.All https://outlook.office365.com/POP.AccessAsUser.Allthis is a correct set of scopes
https://outlook.office.com/IMAP.AccessAsUser.All https://outlook.office.com/POP.AccessAsUser.All
Solution for Root Cause 8
There is no general solution for this root cause, as it will depend on your environment and network.
We have seen situations where some customers had a corporate network scanning all internal traffic coming out of the Jira application, including SSL/TLS protected traffic. For this type of environment, the SSL certificate from the corporate network had to be imported in Jira's Java truststore. Please note that this is just an example of use case, and that your environment and therefore the type of SSL certificate that needs to be imported might be different.
For more information about this type of error and its resolution, you can refer to the KB article Unable to connect to SSL services due to "PKIX Path Building Failed" error.