SSO triggers error "Received invalid SAML response" when attempting to log into Confluence Data Center using Google Chrome
Platform Notice: Data Center - This article applies to Atlassian products on the Data Center platform.
Note that this knowledge base article was created for the Data Center version of the product. Data Center knowledge base articles for non-Data Center-specific features may also work for Server versions of the product, however they have not been tested. Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
Summary
While using Google Chrome Confluence users may receive a "Something went wrong! We couldn't log you in..." error while trying to login to Confluence via SSO. Upon refreshing the browser the users may eventually successfully log in to the application.
Environment
Confluence Data Center
Diagnosis
The following error will appear in the atlassian-confluence.log file:
2021-01-20 01:49:03,936 ERROR [http-nio-8090-exec-45] [impl.web.filter.ErrorHandlingFilter] doFilter Received invalid SAML response: The Response has an InResponseTo attribute: ONELOGIN_d0d1f125-1aff-490f-a00f-04ce49d28a02 while no InResponseTo was expected
Cause
This could be related to the SameSite cookie attribute. The Chrome 80 browser release introduced changes in February 2020 that affect the handling of cross-site cookies. These changes may prevent users from signing in to applications that do not have the proper compatibility.
Solution
For Chrome release 80 or later, till version 90
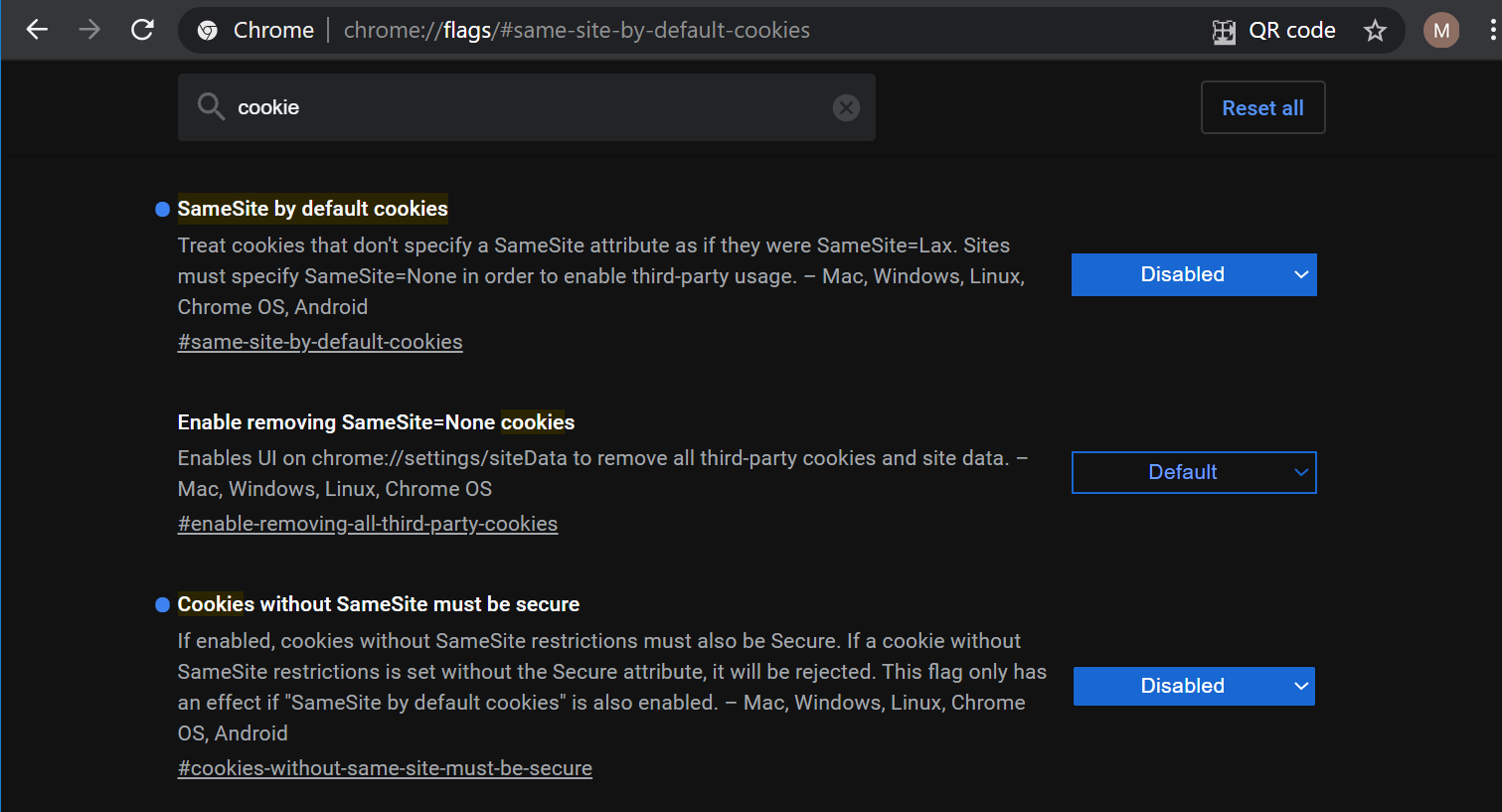
In order to determine if this is the issue, a user can load chrome://flags and set the three SameSite flags to the following values:
For Chrome release 91 or later
As mentioned on the SameSite updates page of the Chromiun 91 Project, the flags in question are enabled by default and have been removed from chrome://flags in new versions.
It is possible to disable the flags using below workarounds:
For Mac
1. Open Terminal on your Mac (you can search for it in Spotlight).
2. Paste the following command:
/Applications/Google\ Chrome.app/Contents/MacOS/Google\ Chrome --disable-features=SameSiteByDefaultCookies,CookiesWithoutSameSiteMustBeSecure3. Press 'Enter'.
This should open Google Chrome with the features 'SameSiteByDefaultCookies' and 'CookiesWithoutSameSiteMustBeSecure' disabled for the current session.
For Windows
1. Press `Win + R` to open the Run dialog box.
2. Type `cmd` and press `Enter` to open Command Prompt.
3. Paste the following command:
"C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --disable-features=SameSiteByDefaultCookies,CookiesWithoutSameSiteMustBeSecure4. Press `Enter`.
This command assumes that Chrome is installed in the default location. If it's not, you'll need to replace `"C:\Program Files (x86)\Google\Chrome\Application\chrome.exe"` with your actual Chrome path.
This will open Google Chrome with the 'SameSiteByDefaultCookies' and 'CookiesWithoutSameSiteMustBeSecure' features disabled for the current session.
Remember, this is a temporary change and will only apply for the current session of Google Chrome.
You need to close all instances of Chrome that are running before executing these command, to ensure the changes take effect.
Permanent Solution
After this change is applied, check if it the problem is fixed.
If so, an Administrator can implement a permanent fix for Confluence by editing the <confluence-install-dir>/conf/context.xml file and adding the following lines below the closing Context tag as follows:
<!-- SAML CHROME SAME-SITE POLICY -->
<CookieProcessor sameSiteCookies="none" />
</Context>This change has to be applied in each node and once this is made perform a rolling restart to apply the update.
Alternate cause and solution
This issue can also be triggered by the SSO plugin being out of date.