Connect to an LDAP directory
You can connect Bitbucket Data Center and Server to an existing LDAP user directory, so that your existing users and groups in an enterprise directory can be used in Bitbucket. The LDAP directory is used for both user authentication and account management.
Bitbucket is able to connect to the following LDAP directory servers:
- Microsoft Active Directory
- Apache Directory Server (ApacheDS) 1.0.x and 1.5.x
- Apple Open Directory (Read-Only)
- Fedora Directory Server (Read-Only Posix Schema)
- Novell eDirectory Server
- OpenDS
- OpenLDAP
- OpenLDAP (Read-Only Posix Schema)
- Generic Posix/RFC2307 Directory (Read-Only)
- Sun Directory Server Enterprise Edition (DSEE)
- Any generic LDAP directory server
Connecting Atlassian Bitbucket to your external directory is not sufficient to allow your users to log in. You must explicitly grant them access to Bitbucket in the global permission screen.
We recommend that you use groups instead of individual accounts when granting permissions.
License considerations
When connecting Bitbucket to an external directory, be careful not to allow access by more users than your Bitbucket license allows. If the license limit is exceeded, your developers will not be able to push commits to repositories, and Bitbucket will display a warning banner. See this FAQ.
Synchronization when Bitbucket is first connected to the LDAP directory
When you first connect Bitbucket to an existing LDAP directory, the Bitbucket internal directory is synchronized with the LDAP directory. User information, including groups and group memberships, is copied across to the Bitbucket directory.
When we performed internal testing of synchronization with an Active Directory server on our local network with 10 000 users, 1000 groups and 200 000 memberships, we found that the initial synchronization took about 5 minutes. Subsequent synchronizations with 100 modifications on the AD server took a couple of seconds to complete. See the option below.
Note that when Bitbucket is connected to an LDAP directory, you cannot update user details in Bitbucket. Updates must be done directly on the LDAP directory, perhaps using a LDAP browser tool such as Apache Directory Studio.
Option - Use LDAP filters to restrict the number of users and groups that are synchronized
You can use LDAP filters to restrict the users and groups that are synchronized with the Bitbucket internal directory. You may wish to do this in order to limit the users or groups that can access Bitbucket, or if you are concerned that synchronization performance may be poor.
For example, to limit synchronization to just the groups named "bitbucket_user" or "red_team", enter the following into the Group Object Filter field (see Group Schema Settings below):
(&(objectClass=group)(|(cn=bitbucket_user)(cn=red_team)))For further discussion about filters, with examples, please see How to write LDAP search filters. Note that you need to know the names for the various containers, attributes and object classes in your particular directory tree, rather than simply copying these examples. You can discover these container names by using a tool such as Apache Directory Studio.
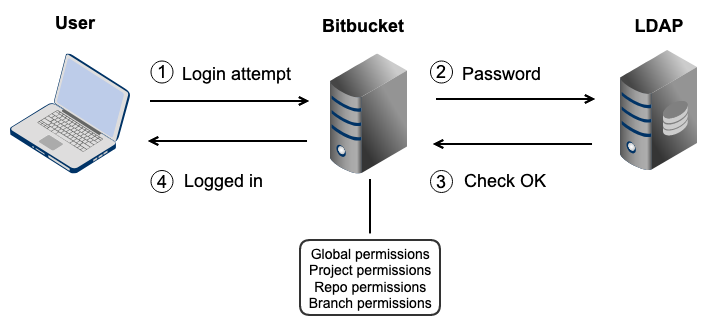
Authentication when a user attempts to log in
When a user attempts to log in to Bitbucket, once synchronization has completed, Bitbucket confirms that the user exists in it's internal directory and then passes the user's password to the LDAP directory for confirmation. If the password matches that stored for the user, LDAP passes a confirmation back to Bitbucket, and Bitbucket logs in the user. During the user's session, all authorizations (i.e. access to Bitbucket resources such as repositories, pull requests and administration screens) are handled by Bitbucket, based on permissions maintained byBitbucket in its internal directory.
Connecting Bitbucket
To connect Bitbucket to an LDAP directory:
- Log in as a user with 'Admin' permission.
- In the Bitbucket administration area, click User Directories (under 'Accounts').
- Click Add Directory and select either Microsoft Active Directory or LDAP as the directory type.
- Configure the directory settings, as described in the tables below.
- Save the directory settings.
- Define the directory order by clicking the arrows next to each directory on the 'User Directories' screen. The directory order has the following effects:
- The order of the directories is the order in which they will be searched for users and groups.
- Changes to users and groups will be made only in the first directory where the application has permission to make changes.
Server settings
Setting | Description |
|---|---|
Name | Enter a meaningful name to help you identify the LDAP directory server. Examples:
|
Directory type | Select the type of LDAP directory that you will connect to. If you are adding a new LDAP connection, the value you select here will determine the default values for many of the options on the rest of screen. Examples:
|
Hostname | The host name of your directory server. Examples:
|
Port | The port on which your directory server is listening. Examples:
|
Use SSL | Check this if the connection to the directory server is an SSL (Secure Sockets Layer) connection. Note that you will need to configure an SSL certificate to use this setting. |
Username | The distinguished name of the user that the application will use when connecting to the directory server. Examples:
By default, all users can read the uSNChanged attribute; however, only administrators or users with relevant permissions can access the Deleted Objects container. The specific privileges required by the user to connect to LDAP are "Bind" and "Read" (user info, group info, group membership, update sequence number, deleted objects), which the user can obtain by being a member of the Active Directory's built-in administrators group. Note that the incremental sync will fail silently if the Active Directory is accessed by a user without these privileges. This has been reported as CWD-3093. |
Password | The password of the user specified above. Note: Connecting to an LDAP server requires that this application log in to the server with the username and password configured here. Passwords are encrypted to enhance security, protecting sensitive credentials from unauthorized access. To guarantee its security, make sure that other processes don't have OS-level read permissions for this application's database or configuration files. |
LDAP schema
Setting | Description |
|---|---|
Base DN | The root distinguished name (DN) to use when running queries against the directory server. Examples:
|
Additional User DN | This value is used in addition to the base DN when searching and loading users. If no value is supplied, the subtree search will start from the base DN. Example:
|
Additional Group DN | This value is used in addition to the base DN when searching and loading groups. If no value is supplied, the subtree search will start from the base DN. Example:
|
If no value is supplied for Additional User DN or Additional Group DN this will cause the subtree search to start from the base DN and, in case of a huge directory structure, could cause performance issues for login and operations that rely on login to be performed.
LDAP permission
Setting | Description |
|---|---|
Read Only | LDAP users, groups and memberships are retrieved from your directory server and can only be modified via your directory server. You cannot modify LDAP users, groups or memberships via the application administration screens. |
Read Only, with Local Groups | LDAP users, groups and memberships are retrieved from your directory server and can only be modified via your directory server. You cannot modify LDAP users, groups or memberships via the application administration screens. However, you can add groups to the internal directory and add LDAP users to those groups. |
Advanced settings
The Manage User Status Locally option, described below, will not work within Bitbucket. Do not enable this option.
BSERV-5129 - Getting issue details... STATUS
Setting | Description |
|---|---|
Enable Nested Groups | Enable or disable support for nested groups. Some directory servers allow you to define a group as a member of another group. Groups in such a structure are called nested groups. Nested groups simplify permissions by allowing sub-groups to inherit permissions from a parent group. |
| Manage User Status Locally | If true, you can activate and deactivate users in Crowd independent of their status in the directory server. |
| Filter out expired users | If true, user accounts marked as expired in Active Directory will be automatically removed. For cached directories, the removal of a user will occur during the first synchronization after the account's expiration date. Note: This is available in Embedded Crowd 2.0.0 and above, but not available in the 2.0.0 m04 release. |
Use Paged Results | Enable or disable the use of the LDAP control extension for simple paging of search results. If paging is enabled, the search will retrieve sets of data rather than all of the search results at once. Enter the desired page size – that is, the maximum number of search results to be returned per page when paged results are enabled. The default is 1000 results. |
Follow Referrals | Choose whether to allow the directory server to redirect requests to other servers. This option uses the node referral (JNDI lookup |
Naive DN Matching | If your directory server will always return a consistent string representation of a DN, you can enable naive DN matching. Using naive DN matching will result in a significant performance improvement, so we recommend enabling it where possible.
|
| Enable Incremental Synchronization | Enable incremental synchronization if you only want changes since the last synchronization to be queried when synchronizing a directory.
If at least one of these conditions is not met, you may end up with users who are added to (or deleted from) the Active Directory not being respectively added (or deleted) in the application. This setting is only available if the directory type is set to "Microsoft Active Directory". |
Update group memberships when logging in | This setting enables updating group memberships during authentication and can be set to the following options:
|
Synchronization Interval (minutes) | Synchronization is the process by which the application updates its internal store of user data to agree with the data on the directory server. The application will send a request to your directory server every x minutes, where 'x' is the number specified here. The default value is 60 minutes. |
Read Timeout (seconds) | The time, in seconds, to wait for a response to be received. If there is no response within the specified time period, the read attempt will be aborted. A value of 0 (zero) means there is no limit. The default value is 120 seconds. |
Search Timeout (seconds) | The time, in seconds, to wait for a response from a search operation. A value of 0 (zero) means there is no limit. The default value is 60 seconds. |
Connection Timeout (seconds) | This setting affects two actions. The default value is 10.
|
User schema settings
Setting | Description |
|---|---|
User Object Class | This is the name of the class used for the LDAP user object. Example:
|
User Object Filter | The filter to use when searching user objects. Example:
More examples can be found in our knowledge base. See How to write LDAP search filters. |
User Name Attribute | The attribute field to use when loading the username. Examples:
NB: In Active Directory, the 'sAMAccountName' is the 'User Logon Name (pre-Windows 2000)' field. The User Logon Name field is referenced by 'cn'. |
User Name RDN Attribute | The RDN (relative distinguished name) to use when loading the username. The DN for each LDAP entry is composed of two parts: the RDN and the location within the LDAP directory where the record resides. The RDN is the portion of your DN that is not related to the directory tree structure. Example:
|
User First Name Attribute | The attribute field to use when loading the user's first name. Example:
|
User Last Name Attribute | The attribute field to use when loading the user's last name. Example:
|
User Display Name Attribute | The attribute field to use when loading the user's full name. Example:
|
User Email Attribute | The attribute field to use when loading the user's email address. Example:
|
User Password Attribute | The attribute field to use when loading a user's password. Example:
|
| User Unique ID Attribute | The attribute used as a unique immutable identifier for user objects. This is used to track username changes and is optional. If this attribute is not set (or is set to an invalid value), user renames will not be detected — they will be interpreted as a user deletion then a new user addition. This should normally point to a UUID value. Standards-compliant LDAP servers will implement this as 'entryUUID' according to RFC 4530. This setting exists because it is known under different names on some servers, e.g. 'objectGUID' in Microsoft Active Directory. |
Group schema settings
Setting | Description |
|---|---|
Group Object Class | This is the name of the class used for the LDAP group object. Examples:
|
Group Object Filter | The filter to use when searching group objects. Example:
|
Group Name Attribute | The attribute field to use when loading the group's name. Example:
|
Group Description Attribute | The attribute field to use when loading the group's description. Example:
|
Membership schema settings
Setting | Description |
|---|---|
Group Members Attribute | The attribute field to use when loading the group's members. Example:
|
User Membership Attribute | The attribute field to use when loading the user's groups. Example:
|
Use the User Membership Attribute, when finding the user's group membership | Check this if your directory server supports the group membership attribute on the user. (By default, this is the '
|
Use the User Membership Attribute, when finding the members of a group | Check this if your directory server supports the user membership attribute on the group. (By default, this is the '
|