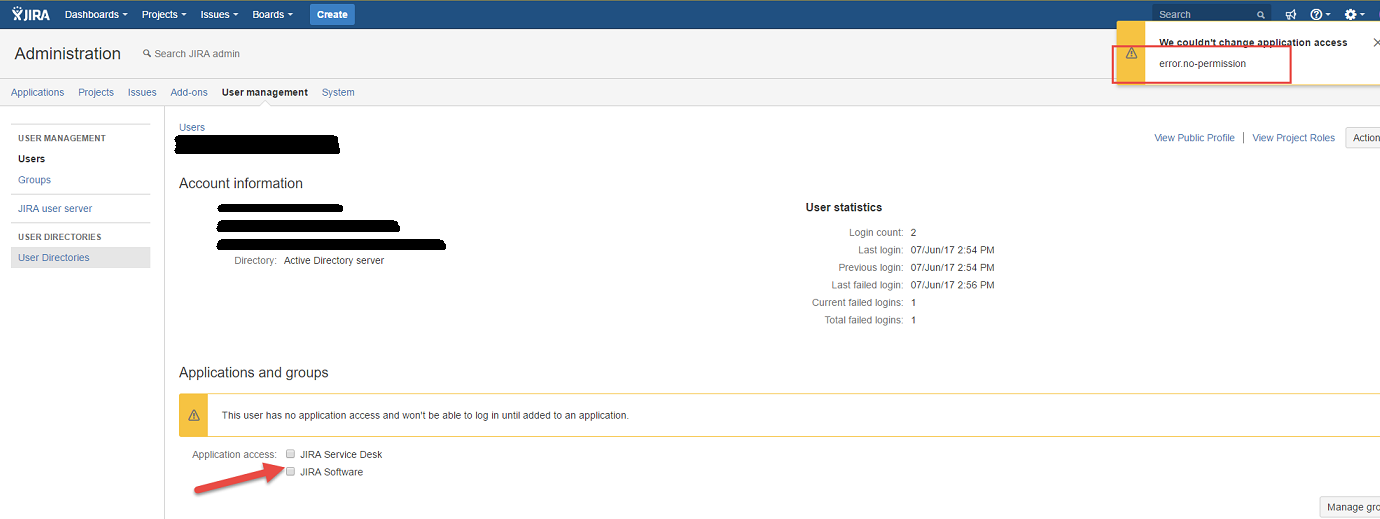
Associating users to Applications or Group ends up with error.no-permission
Platform notice: Server and Data Center only. This article only applies to Atlassian products on the Server and Data Center platforms.
Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
Symptoms
You have configured an internal directory and an LDAP directory with the permission "Read Only, with Local Groups" with no default group memberships. Configuration was successful and synchronization was without any problem. When you try to give Application Access to an LDAP user, it fails with the error "We couldn't change application access. error.no-permission". When you try to associate the user with the jira-software-users group from the UI, you are faced with the same error.
Cause
There is a duplicate jira-software-users groups in the LDAP server and the system is attempting to associate the user with LDAP group which is read only and hence will fail. This can be confirmed from duplicate group names across the Internal Directory and the Active Directory User Directory:
select * from cwd_group where lower_group_name in ('jira-software-users', 'jira-servicedesk-users')Resolution
- If you want to have the groups in both the JIRA application and LDAP, then better just associate the users with the necessary group from LDAP right from the beginning.
- Enable write permission on the LDAP server and edit the directory to have the "read/write" permission.
- If the group that is duplicated in the JIRA application is not very useful in LDAP, you may want to consider deleting the group and then re-synchronize your directory or
- Specifying an invalid LDAP Group filter so no LDAP groups are synced into JIRA. e.g. Change the JIRA User Directory Group Filter to: (objectCategory=GroupNotRequired)
Please see our Troubleshooting LDAP User Management documentation for further assistance with diagnosing LDAP problems.