How to setup Okta as a user provisioner to Jira through JIT
Platform Notice: Data Center - This article applies to Atlassian products on the Data Center platform.
Note that this knowledge base article was created for the Data Center version of the product. Data Center knowledge base articles for non-Data Center-specific features may also work for Server versions of the product, however they have not been tested. Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
Summary
Okta is used as a SAML/SSO provider, but it can also be set as a user provisioner to Jira, which is our goal with this article: a straightforward step-by-step to setup Okta to provision users, create them automatically in login through JIT.
Essential prerequisites:
- Use the SSO for Atlassian Server and Data Center App,
- Be familiar with Okta configuration, including attributes mapping. And
- Okta SAML shall be already setup in accordance with How to configure Jira Software Data Center for SAML 2.0 SSO with Okta article.
Please notice this article doesn't intend to be a source of truth on setting up JIT with Okta. If you have any point not explored in this article, please contact both the Okta and Atlassian support teams.
Solution
With Okta and Jira already setup as SAML provider for Jira, setup Jira to use Okta with JIT:
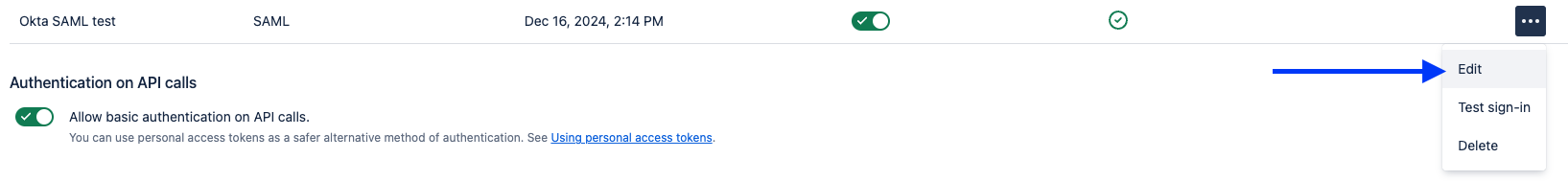
- As Jira administrator, go to Admin > Authentication methods > Edit
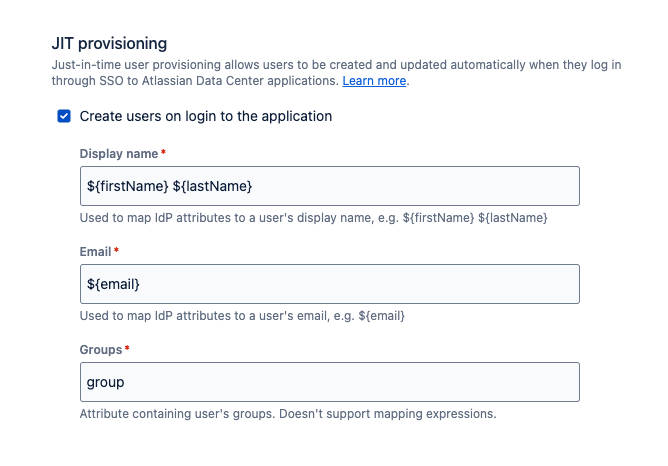
- On the JIT provisioning part, mark the "Create users on login to the application", and set the attributes as
- Display name: ${firstName} ${lastName} (or any other attribute variable name. If a different one is used, just record to use the same later!)
- Email: ${email}
- Groups: group (notice it cannot be a mapping expression)
- Save this configuration
Now login to Okta admin console, and:
- On Jira application edit the SAML settings
- Go to Configure SAML (the second page) "Attribute Statements" part and setup the attributes that need to be sent to Jira. Notice that we are setting the same variables/attributes set in Jira SAML settings, above (again, if different strings for attributes were used in Jira, the same shall be set in Okta).
- The attribute Name firstName shall be set with Value user.firstName
- The attribute Name lastName shall be set with Value user.lastName
- The attribute Name email shall be set with Value user.email
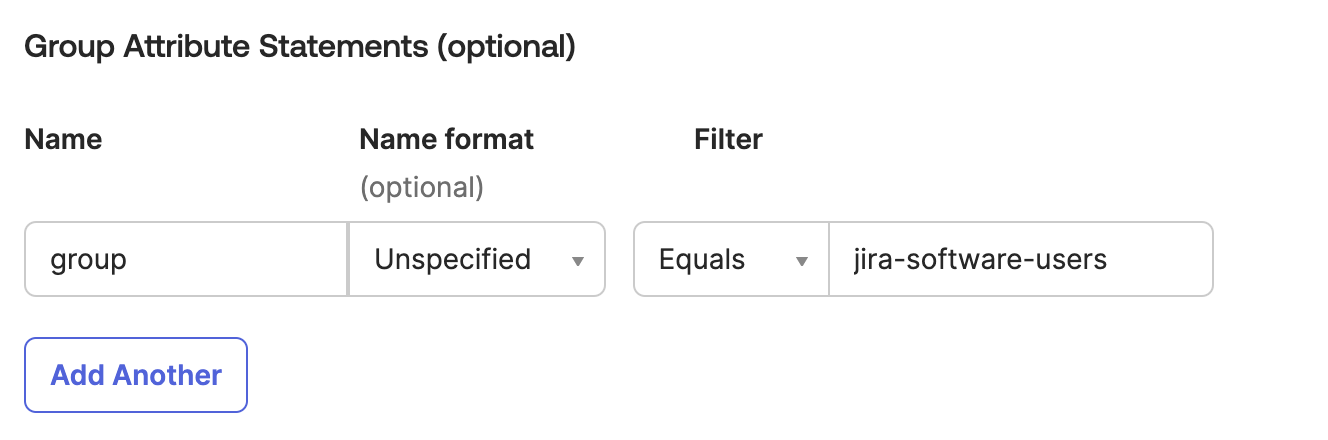
- Similarly to "attribute statement", go to "Group Attribute Statements" and setup the group attribute to be sent
- The group attribute Name shall be set as group and the Filter may be set as your needs, in this example it will only look for users in group jira-software-users, and this value will be sent to Jira
Important: at lease one application access group shall return from the group filter. Otherwise the user will not be able to login to Jira.
- The group attribute Name shall be set as group and the Filter may be set as your needs, in this example it will only look for users in group jira-software-users, and this value will be sent to Jira
- Last, if not set already, go to Directory > Groups, setup the group (in our example the jira-software-users) and add users to it
Now, it's all set! Try to login to your Jira using Okta, and observe if the user is created and can access the tool as expected.
Common issues
Once Jira requires that the attributes mapped to Display Name, email and group are set (they shall not be blank or invalid), a very common issue is the "attribute could not be found". As the example below, we can observe that the attribute attribute-name did not match the value expected by Jira.
/plugins/servlet/samlconsumer ERROR anonymous 1011x7977x1 6y8qvm 0:0:0:0:0:0:0:1 /plugins/servlet/samlconsumer [c.a.p.a.s.web.filter.ErrorHandlingFilter] [UUID: 53c40c1d-ee6a-47e5-a5cc-ce47e2fbefe9] Attribute [attribute-name] could not be found
com.atlassian.plugins.authentication.sso.web.usercontext.impl.jit.JitException: Attribute [attribute-name] could not be found
at com.atlassian.plugins.authentication.sso.web.usercontext.impl.jit.mapping.SamlUserDataFromIdpMapper.mapGroups(SamlUserDataFromIdpMapper.java:54)
at com.atlassian.plugins.authentication.sso.web.usercontext.impl.jit.mapping.SamlUserDataFromIdpMapper.mapUser(SamlUserDataFromIdpMapper.java:26)
at com.atlassian.plugins.authentication.sso.web.saml.SamlConsumerServlet.doPost(SamlConsumerServlet.java:104)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:555)
...When that happens, double check if the attribute mapped in Jira (the ${firstName}, ${lastName}, ${email}, and group, in our example) are the same variable/attributes set in Okta. If you have questions on mapping attributes in Okta, please engage Okta support.