How to view SAML responses in your browser for troubleshooting
Platform notice: Server and Data Center only. This article only applies to Atlassian products on the Server and Data Center platforms.
Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
Purpose
The following guide describes some processes that can be used to troubleshoot SAML 2.0 related configurations with Atlassian applications from your browser. These are useful when integrating SAML with your application and can help you pinpoint any misconfigurations on the IdP side. Note that the data provided in the examples will differ from your settings, so keep in mind this is for information purposes only.
Firefox
Manual Approach:
Open the developer console. You can generally do this by going to the Firefox settings and clicking on "Developer"
- Click on "Network"
In the upper right of the developer tools window, click Toolbox Options (the small gear icon). Under Common Preferences, select Enable persistent logs.
Go back to the Network tab.
Reproduce the SAML issue.
Look for a POST method with a saml consumer file in the table.
Select that row.
- Review the data in the Headers, Cookies and Params tabs to make sure the calls are being directed properly.
Tool:
Download the tool SAML Tracer for Firefox.
- Open the tool and reproduce the SAML issue.
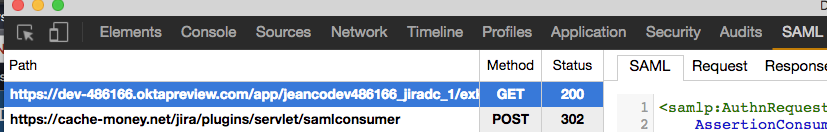
- The tool will highlight all SAML calls for you, so that you can easily select the calls:
Select the GET call and click on SAML to get the request the application is sending over to the IdP. This is useful for validating that the "Assertion Consumer Service URL" and "Identity provider single sign-on URL" values match the AssertionConsumerServiceURL and Destination values, respectively, and are being routed properly.
<samlp:AuthnRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ID="ONELOGIN_31984fcf-88f9-43d6-9124-276096eec5cf" Version="2.0" IssueInstant="2017-01-27T16:56:09Z" Destination="https://dev-486166.oktapreview.com/app/jeancodev486166_jiradc_1/exk9awjfupbFE8VQp0h7/sso/saml" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" AssertionConsumerServiceURL="https://jira.example.com/jira/plugins/servlet/samlconsumer" > <saml:Issuer>https://jira.example.com/jira</saml:Issuer> </samlp:AuthnRequest>- Select the POST call and click on SAML. This is useful to confirm that the:
-X509 certificate is correct
-Conditions such as AudienceRestrictions are not preventing SSO/SAML from working. Audience restrictions are validity conditions for an assertion, so it's possible that it may cause sign-in issues.
Chrome
Manual Approach:
Open the developer tools. You can generally do this by going to the Chrome settings and clicking on More Tools --> Developer Tools.
Select the Network tab, and then select Preserve log.
Reproduce the SAML issue.
Look for a SAML Post with a samlconsumer call in the developer console pane.
Select that row, and then view the Headers tab at the bottom.
Tool:
Download the tool SAML Chrome Panel Tool for Chrome. This will add a SAML option to the developer tools in Chrome.
- Open the tool and reproduce the SAML issue.
- This will automatically intercept the SAML GET and POST commands for you
Select the GET call and click on SAML to get the request the application is sending over to the IdP. This is useful for validating that the "Assertion Consumer Service URL" and "Identity provider single sign-on URL" values match the AssertionConsumerServiceURL and Destination values, respectively, and are being routed properly
<samlp:AuthnRequest AssertionConsumerServiceURL="https://jira.example.com/jira/plugins/servlet/samlconsumer" Destination="https://dev-486166.oktapreview.com/app/jeancodev486166_jiradc_1/exk9awjfupbFE8VQp0h7/sso/saml" ID="ONELOGIN_2f01b3cb-fb02-424a-8c3a-0d9a622e5641" IssueInstant="2017-01-27T17:26:09Z" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Version="2.0" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"> <saml:Issuer>https://jira.example.com/jira</saml:Issuer> </samlp:AuthnRequest>
Select the POST call and click on SAML. This is useful to confirm that the:
<?xml version="1.0" encoding="UTF-8"?><saml2p:Response xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol" Destination="https://jira.example.com/jira/plugins/servlet/samlconsumer" ID="id14163116055324067385078961" InResponseTo="ONELOGIN_45892382-b1cf-48c7-8bea-22687d0373b4" IssueInstant="2017-01-27T18:22:20.541Z" Version="2.0"><saml2:Issuer xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion" Format="urn:oasis:names:tc:SAML:2.0:nameid-format:entity">http://www.okta.com/exk9awjfupbFE8VQp0h7</saml2:Issuer><ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:SignedInfo><ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/><ds:SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256"/><ds:Reference URI="#id14163116055324067385078961"><ds:Transforms><ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/><ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/></ds:Transforms><ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"/><ds:DigestValue>YCy7olQWX1AanMEQEbqBpaYBD6rifGhonokAbs8XumU=</ds:DigestValue></ds:Reference></ds:SignedInfo><ds:SignatureValue>jUeDh2vriRHni8voGciPMGS6qU2NbwHtJQAIbpKqr9EIrvbZv4KLrZGrXx9xLTxymwzJnYTYsGpgHAzV0ZMAL0oxOgqfPAOZlBeW0mq3hpCT7gpDF2iahs3lAu5+908TnHuftMxPCjZNXT08LAtLlarRWVoXoFBVAMDxm3izKbPIYZkHwqZQ1G9LqcP/xP++eKdd0B2tmSI8IfPWqyl8am1k23N9PypIJ/TJCBlQWm0rEnrURMAYkBbbYfadIxQMyHHLRrvFnosSoj+NLCt64WLGkimTn75/TmCP/7UeFDT5/tHGBk+ngOs1MPKEW4mHg1Rpdn+lnEVSbGLgV8PkJQ==</ds:SignatureValue><ds:KeyInfo><ds:X509Data><ds:X509Certificate>MIIDpDCCAoygAwIBAgIGAVl1oNWbMA0GCSqGSIb3DQEBBQUAMIGSMQswCQYDVQQGEwJVUzETMBEG
A1UECAwKQ2FsaWZvcm5pYTEWMBQGA1UEBwwNU2FuIEZyYW5jaXNjbzENMAsGA1UECgwET2t0YTEU
MBIGA1UECwwLU1NPUHJvdmlkZXIxEzARBgNVBAMMCmRldi00ODYxNjYxHDAaBgkqhkiG9w0BCQEW
DWluZm9Ab2t0YS5jb20wHhcNMTcwMTA2MjExMjExWhcNMjcwMTA2MjExMzExWjCBkjELMAkGA1UE
BhMCVVMxEzARBgNVBAgMCkNhbGlmb3JuaWExFjAUBgNVBAcMDVNhbiBGcmFuY2lzY28xDTALBgNV
BAoMBE9rdGExFDASBgNVBAsMC1NTT1Byb3ZpZGVyMRMwEQYDVQQDDApkZXYtNDg2MTY2MRwwGgYJ
KoZIhvcNAQkBFg1pbmZvQG9rdGEuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA
n5+MbxEb0rRA5kDBxVvzNRO3otJS7UMB3ldTEqivmieXvkXiSLjVYQJr7gbg+OYAX12V35HmrIs6
RiT/d4trsePI09hRjQD2eMXsd11v1eKmoyAbsV026LZTHoVpXZQyeK383chJLEp2G6lRVdA/uFpP
j5OCSiB5jVhEdRXymbfeESecMbh5YJu9H025sDBiqyzDHmZXunPdmJ0fyFpY9Q98bMfi7KUICHff
lncSYQRDYax17wTO/2Nu4akWVESiBaedBlXAKuEOoB26ysxbQiUATOJTKodiGydyxLAlk2DV+Uzz
DAeN8mQw7y4MArrSDqTWnTbtg3SJl6e0Ho/CGQIDAQABMA0GCSqGSIb3DQEBBQUAA4IBAQBNy/LR
G85t3nuk4bnh2XRWtOXlSKtq6fVMAtJ4kd8vxB8M8DyFWDIaoXTd35COs1p2LX176hdBKjgau8Ux
NUOJ3MIOw8qQAwFWguBHFWYhrcgDCVtCvz3wLIBRZehW/tX2ah+M8ATsn8oLPHaL2W11Z0JOiEcV
IdAu6CyR1iDcVjCT7DV3h8aUWaLjfnfcJasEqiTEs2DH1d8E+GdW/lWaGiAdVlnxmxv5rvkwFxvZ
DJyk2VPxZmFVdK16cUbPgnk5Bge7wnNaQZOUBmUZKAKmzeA+22lhKPpv8IGTIwEpcoUHggAdhvrT
HfcvAs4OyFQgeaBA5//UjZVa/MfAFmqP</ds:X509Certificate></ds:X509Data></ds:KeyInfo></ds:Signature><saml2p:Status xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol"><saml2p:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success"/></saml2p:Status><saml2:Assertion xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion" ID="id141631160553688781645743787" IssueInstant="2017-01-27T18:22:20.541Z" Version="2.0"><saml2:Issuer Format="urn:oasis:names:tc:SAML:2.0:nameid-format:entity" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">http://www.okta.com/exk9awjfupbFE8VQp0h7</saml2:Issuer><ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:SignedInfo><ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/><ds:SignatureMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256"/><ds:Reference URI="#id141631160553688781645743787"><ds:Transforms><ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/><ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/></ds:Transforms><ds:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"/><ds:DigestValue>J/NqLATHdaZyZ5sZVzyXMJFyC7hoCaHykvK+cNHWUqg=</ds:DigestValue></ds:Reference></ds:SignedInfo><ds:SignatureValue>COtWGeHTJvXkvOgIRURPGI146AosRK/s81v9z11zAZ5Qzv0Uky9UYa4oTxI105yGUocwDkVsn0aDTszy6G0A3g4O+ERHyJ5cXil7p/NHmhZmId6bl/hTsp7zyTKmMQnaSr0B7MeYDGKjf9GlQNg+jnSzcKG7ncSeDUgLgNwpPypsipto76NLMx7z1dP20Mtq/+1fj4P2iv0/N5lJOOsOmtgUBXq9RUAv45QP7cHCK7JGf218+NVePoI0+Z2WLoe16YZCw68B2KZBB8E0qs9qXXZAeWZZQcDuVz8WgYIlhvgqgU1KlChA9j6OGjI2m6GVuQZtuhBONCz0gbuEpdPSdQ==</ds:SignatureValue><ds:KeyInfo><ds:X509Data><ds:X509Certificate>MIIDpDCCAoygAwIBAgIGAVl1oNWbMA0GCSqGSIb3DQEBBQUAMIGSMQswCQYDVQQGEwJVUzETMBEG
A1UECAwKQ2FsaWZvcm5pYTEWMBQGA1UEBwwNU2FuIEZyYW5jaXNjbzENMAsGA1UECgwET2t0YTEU
MBIGA1UECwwLU1NPUHJvdmlkZXIxEzARBgNVBAMMCmRldi00ODYxNjYxHDAaBgkqhkiG9w0BCQEW
DWluZm9Ab2t0YS5jb20wHhcNMTcwMTA2MjExMjExWhcNMjcwMTA2MjExMzExWjCBkjELMAkGA1UE
BhMCVVMxEzARBgNVBAgMCkNhbGlmb3JuaWExFjAUBgNVBAcMDVNhbiBGcmFuY2lzY28xDTALBgNV
BAoMBE9rdGExFDASBgNVBAsMC1NTT1Byb3ZpZGVyMRMwEQYDVQQDDApkZXYtNDg2MTY2MRwwGgYJ
KoZIhvcNAQkBFg1pbmZvQG9rdGEuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA
n5+MbxEb0rRA5kDBxVvzNRO3otJS7UMB3ldTEqivmieXvkXiSLjVYQJr7gbg+OYAX12V35HmrIs6
RiT/d4trsePI09hRjQD2eMXsd11v1eKmoyAbsV026LZTHoVpXZQyeK383chJLEp2G6lRVdA/uFpP
j5OCSiB5jVhEdRXymbfeESecMbh5YJu9H025sDBiqyzDHmZXunPdmJ0fyFpY9Q98bMfi7KUICHff
lncSYQRDYax17wTO/2Nu4akWVESiBaedBlXAKuEOoB26ysxbQiUATOJTKodiGydyxLAlk2DV+Uzz
DAeN8mQw7y4MArrSDqTWnTbtg3SJl6e0Ho/CGQIDAQABMA0GCSqGSIb3DQEBBQUAA4IBAQBNy/LR
G85t3nuk4bnh2XRWtOXlSKtq6fVMAtJ4kd8vxB8M8DyFWDIaoXTd35COs1p2LX176hdBKjgau8Ux
NUOJ3MIOw8qQAwFWguBHFWYhrcgDCVtCvz3wLIBRZehW/tX2ah+M8ATsn8oLPHaL2W11Z0JOiEcV
IdAu6CyR1iDcVjCT7DV3h8aUWaLjfnfcJasEqiTEs2DH1d8E+GdW/lWaGiAdVlnxmxv5rvkwFxvZ
DJyk2VPxZmFVdK16cUbPgnk5Bge7wnNaQZOUBmUZKAKmzeA+22lhKPpv8IGTIwEpcoUHggAdhvrT
HfcvAs4OyFQgeaBA5//UjZVa/MfAFmqP</ds:X509Certificate></ds:X509Data></ds:KeyInfo></ds:Signature><saml2:Subject xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion"><saml2:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">ajean1899@gmail.com</saml2:NameID><saml2:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"><saml2:SubjectConfirmationData InResponseTo="ONELOGIN_45892382-b1cf-48c7-8bea-22687d0373b4" NotOnOrAfter="2017-01-27T18:27:20.541Z" Recipient="https://jira.example.com/jira/plugins/servlet/samlconsumer"/></saml2:SubjectConfirmation></saml2:Subject><saml2:Conditions NotBefore="2017-01-27T18:17:20.541Z" NotOnOrAfter="2017-01-27T18:27:20.541Z" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion"><saml2:AudienceRestriction><saml2:Audience>https://jira.example.com/jira</saml2:Audience></saml2:AudienceRestriction></saml2:Conditions><saml2:AuthnStatement AuthnInstant="2017-01-27T18:22:20.541Z" SessionIndex="ONELOGIN_45892382-b1cf-48c7-8bea-22687d0373b4" xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion"><saml2:AuthnContext><saml2:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml2:AuthnContextClassRef></saml2:AuthnContext></saml2:AuthnStatement></saml2:Assertion></saml2p:Response>
Safari
Manual Approach:
Enable Web Inspector in Safari. Open the Preferences window, select the Advanced tab, and then select Show Develop menu in the menu bar.
Now you can open Web Inspector. Click Develop, then select Show Web Inspector.
Select the Resources tab.
Reproduce the issue.
Look for the SAML requests
Look for a SAML Post with a samlconsumer call in the developer console pane.
Mappings to note:
The following mappings can help in troubleshooting issues that may be caused by misconfigurations, proxies, network:
- SAML issuer from the POST command needs to match the Single-Sign-on Issuer URL configured in the Atlassian application:
Example:
<saml2:Issuer
Format="urn:oasis:names:tc:SAML:2.0:nameid-format:entity"
xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">http://www.okta.com/exk9awjfupbFE8VQp0h7
</saml2:Issuer>
-
GET:
Destination="https://dev-486166.oktapreview.com/app/jeancodev486166_jiradc_1/exk9awjfupbFE8VQp0h7/sso/saml
POST:
Destination="https://jira.example.com/jira/plugins/servlet/samlconsumer"
-The X509 certificate needs to match between the POST command and the one configured in the Atlassian application