"No subject alternative DNS name found", Certificate with correct hostname is imported.
Platform notice: Server and Data Center only. This article only applies to Atlassian products on the Server and Data Center platforms.
Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
For an Atlassian application to be able to successfully establish SSL connection with LDAP, the certificate for the directory must be trusted. Typically, this certificate is imported into the Java stores for trusted certificates, in a file called a keystore. The default keystore file is called cacerts and it lives in the jre\lib\security sub-directory of your Java installation.
Errors
The connection to the LDAP fails with the an error "handling exception: javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: No subject alternative DNS name matching DOMAIN.COM found."
nested exception is javax.naming.CommunicationException: DOMAIN.COM:636 [Root exception is javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: No subject alternative DNS name matching DOMAIN.COM found.]=Cause 1
The LDAP server uses a different certificate compared to what is imported into the Java environment.
Although this is rare, the LDAP server uses a different server certificate to communicate.
it is possible that the LDAP server, either has multiple server certificates
OR the certificate imported in Java, is no longer present on the LDAP server.
Cause 2
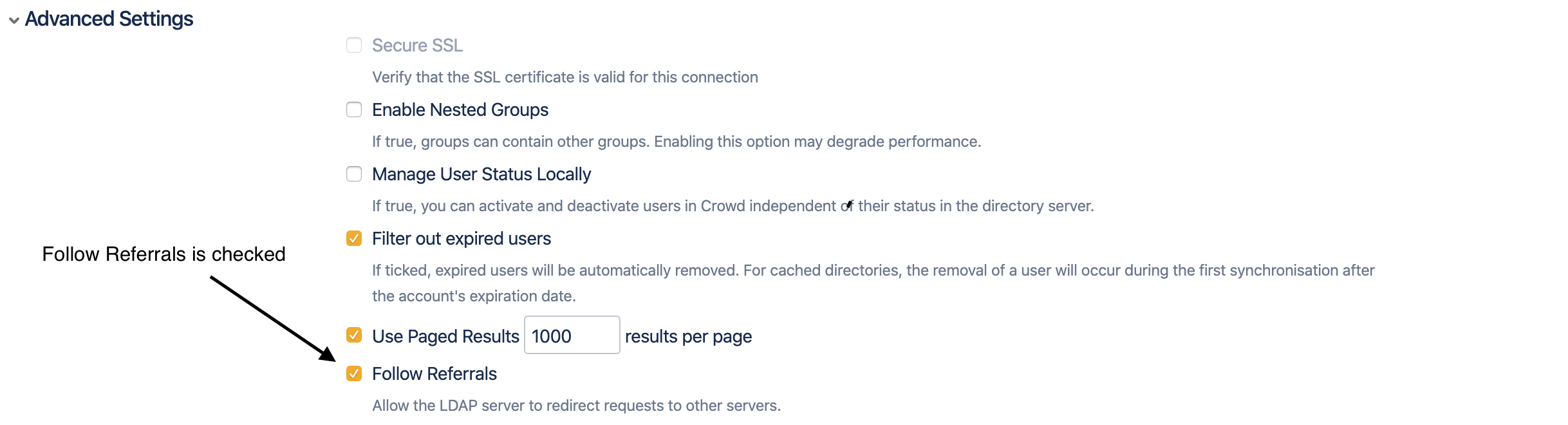
Follow referral is enabled.
By default, "Follow Referrals" is turned on.
Certificate requirement
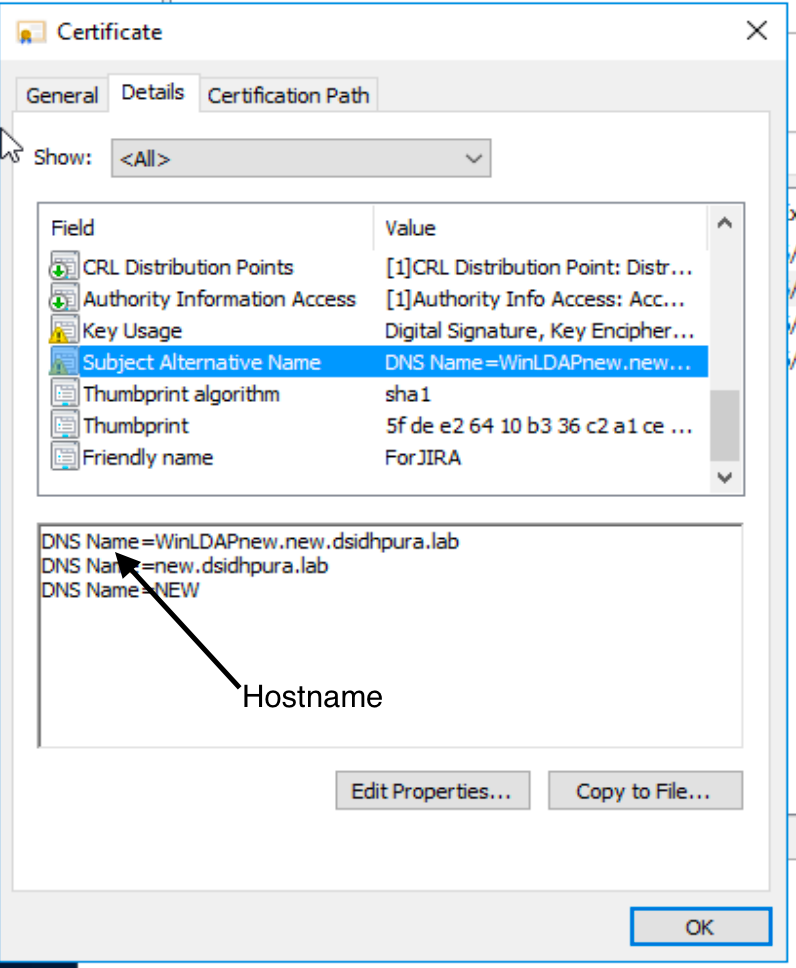
Subject name of the certificate should match the host name of the Directory server mentioned in the User Directory configuration page.
The certificate should contain the LDAP server name.
The certificate should be imported into JAVA runtime environment. Below command can be used.
Please replace "server-certificate.crt" with actual certificate name.
1keytool -importcert -keystore .\jre\lib\security\cacerts -file server-certificate.crt
Jira will need to be restarted to identify the newly imported certificate.
The article Configuring an SSL connection to Active Directory discusses the steps in detail.
Subject Name from the certificate
Hostname from the User Directory configuration
Solution 1
To get certificate used by the LDAP server, enable to the following debug logging.
Once the certificate used LDAP server is identified, import the certificate into the Java environment.
Enable Logging
Add the following to setenv.sh in JVM_SUPPORT_RECOMMENDED_ARGS
"-Djavax.net.debug=all"
Restart Jira.
Check the catalina log file for SSL handshake information
Snippet from the logs
With the above logging enabled, the catalina.out, would log the certificate being received for the connection.
1 2 3 4 5 6 7 8 9 10 11 12 chain [0] = [ [ Version: V3 Subject: CN=WinLDAPnew.new.dsidhpura.lab Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11 Key: Sun RSA public key, 2048 bits public exponent: 65537 Validity: [From: Tue May 12 19:07:25 IST 2020, To: Wed May 12 19:07:25 IST 2021] Issuer: CN=new-WINLDAPNEW-CA, DC=new, DC=dsidhpura, DC=lab SerialNumber: [ 12000000 05123d75 38577613 fb000000 000005]- Below is the certificate in the Java environment
1 2 3 4 5 6 7 Alias name: ldaps Creation date: 12 May, 2020 Entry type: trustedCertEntry Owner: Issuer: CN=new-WINLDAPNEW-CA, DC=new, DC=dsidhpura, DC=lab Serial number: 120000000454d67e7f8f53f1c1000000000004Notice the serial numbers are different between the certificate received for communication and certificate imported into Java.
LDAP server certificate SerialNumber: 1200000005123d7538577613fb000000000005
Java environment certificate Serial number: 120000000454d67e7f8f53f1c1000000000004
Solution 2
With follow referral enabled.
- The DNS name resolution for the domain name should resolve to LDAP server, for which certificate is imported in the Java environment.
- Using the screenshots from this article, the Domain name would be new.dsidhpura.lab.
- This DNS name should resolve the LDAP server for which the certificate is imported in the Java environment.