Use SSH keys in Bitbucket Pipelines
You'll want to set up an SSH key in Bitbucket Pipelines if:
- your build needs to authenticate with Bitbucket or other hosting services to fetch private dependencies.
- your deployment needs to authenticate with a remote host or service before uploading artifacts.
- you want builds to use tools such as SSH, SFTP or SCP.
An SSH public and private key pair must be added to the Bitbucket Cloud repository and the public key must be added to the remote service or machine.
When you set an SSH key on a Bitbucket repository, all users with write access to the repo will have access to the remote host.
You should be able to push and pull to your Bitbucket Cloud repo with no problems. But, if you need to use SSH, for example, to use a bot account, or when branch permissions are enabled, see Set up an SSH key.
For SSH with Bitbucket repos see:
Not all available Docker images have SSH installed by default. If you are using the default pipelines image you'll be fine, but if you need to specify your own image, make sure SSH is either already installed, or install it with your script.
For example, depending on your image, including in your script:
apt-get update -y
apt-get install -y ssh
Step 1: Add an SSH key in Bitbucket
We recommend that you generate a new SSH key pair, but you can use an existing key pair if your key requirements differ from the Bitbucket 2048-bit RSA keys. Whichever way you add an SSH key, the private key is automatically added to the build pipeline (as an additional SSH key), and doesn't need to be specified in the bitbucket-pipelines.yml file.
If your Docker image already has an SSH key your build pipeline can use that key, and you don't need to add an SSH key in this step – go to Step 2!
Any SSH key you use in Pipelines should not have a passphrase.
Note that Bitbucket Pipelines supports one SSH key per repository. If you need to use more than one key, you can add them as secured Bitbucket Pipelines environment variables, and reference them in the bitbucket-pipelines.yml file. See the Use multiple SSH keys section below.
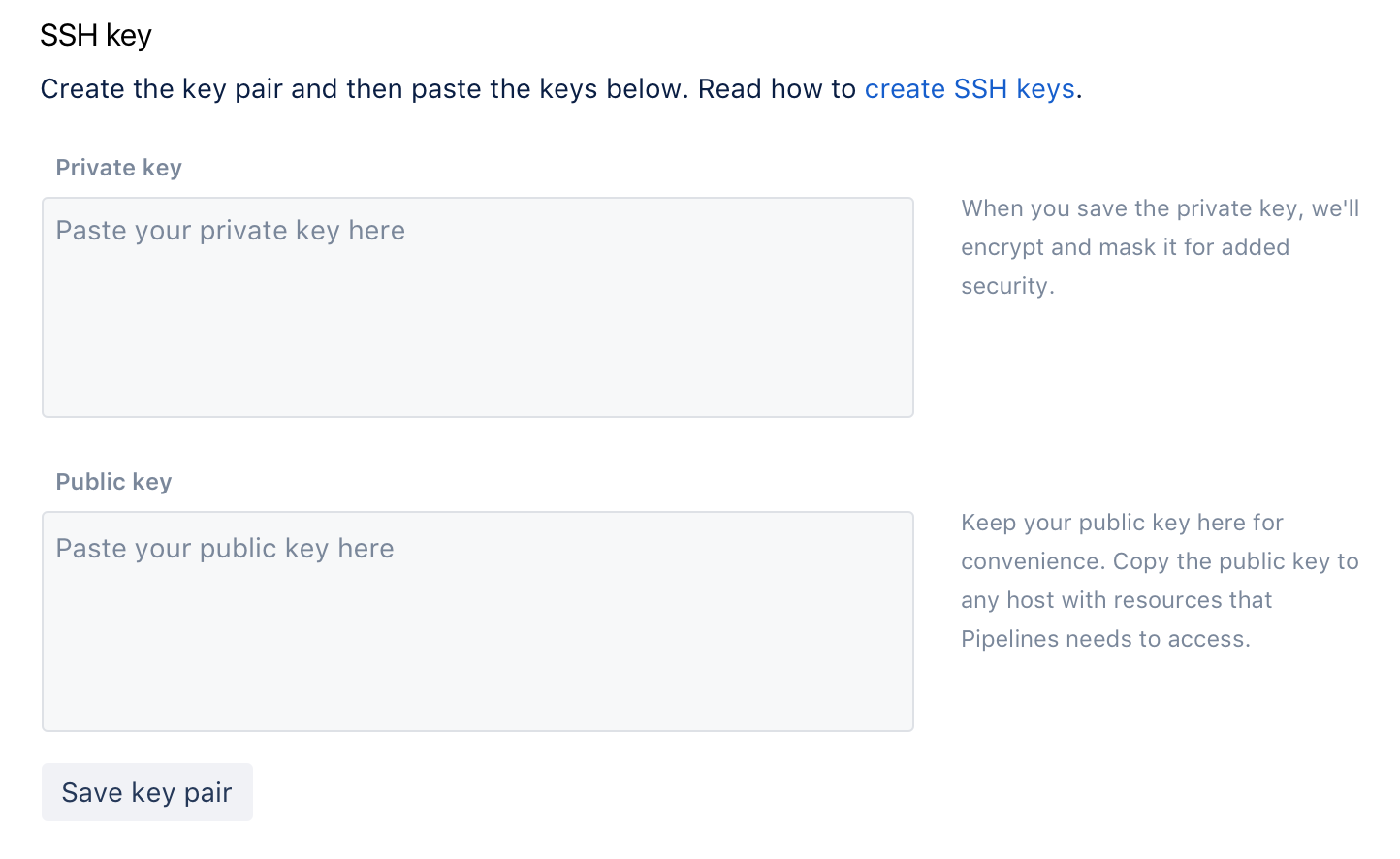
To generate a new SSH key pair (recommended):
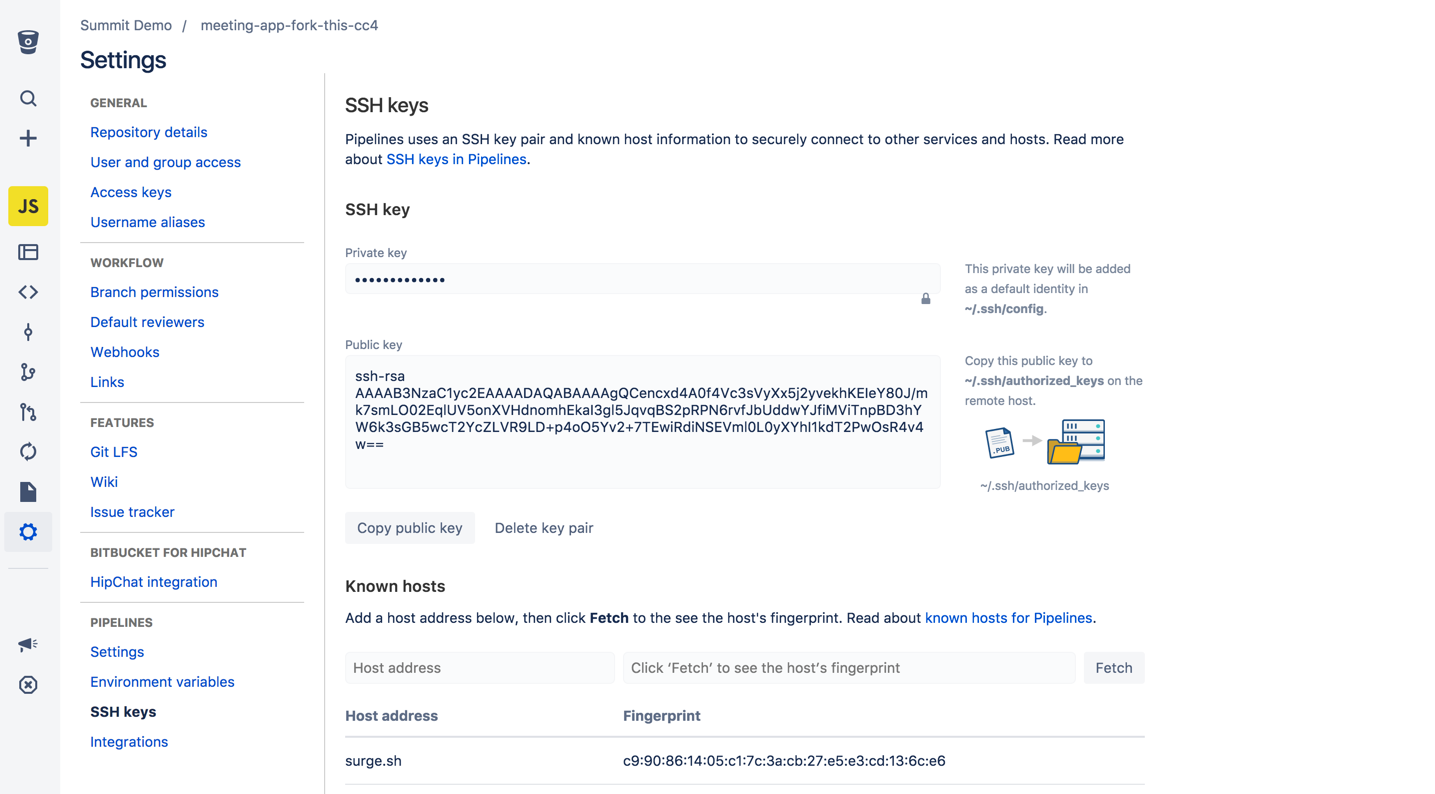
- In the repository Settings, go to SSH keys under 'Pipelines'.
- Click Generate keys to create a new SSH key pair.
Now go to Step 2 below.
To add an existing key pair:
You can use an existing key pair if your key requirements differ from the Bitbucket 2048-bit RSA keys.
For security reasons, you should never add your own personal SSH key – you should use an existing bot key instead.
Step 2: Update the known hosts
Pipelines provides a way for you to store, and inspect, the fingerprint of a remote host, along with the host address. This allows you to visually verify that the public key presented by a remote host actually matches the identity of that host, to help you detect spoofing and man-in-the-middle attacks. It also means that future communications with that host can be automatically verified.
In the repository Settings, go to SSH keys, and add the address for the known host. Click Fetch to see the host's fingerprint:
Note that Bitbucket Pipelines automatically adds the fingerprint for the Bitbucket and GitHub sites to all pipelines (but doesn't display that in the UI shown above).
Step 3: Add the public key to a remote host
You must install the public key on the remote host before Pipelines can authenticate with that host. If you want your Pipelines builds to be able to access other Bitbucket repos, you need to add the public key to that repo.
Remote hosts
If you have SSH access to the server, you can use the ssh-copy-id command. Typically, the command appends the key to the ~/.ssh/authorized_keys file on the remote host:
$ ssh-copy-id -i my_ssh_key user@hostTest the SSH access to the server:
ssh -i ~/.ssh/my_ssh_key user@hostIf you are creating, rather than modifying the .ssh files you may need to change their permissions
- chmod 700 ~/.ssh
- chmod 600 ~/.ssh/authorized_keys
Other Bitbucket Cloud repositories
If you want your Pipelines builds to be able to access a different Bitbucket repository (other than the repo where the builds run):
- Add an SSH key to the settings for the repo where the build will run, as described in Step 1 above (you can create a new key in Bitbucket Pipelines or use an existing key).
- Add the public key from that SSH key pair directly to settings for the other Bitbucket repo (i.e. the repo that your builds need to have access to).
See Access keys for details on how to add a public key to a Bitbucket repo.
Use multiple SSH keys in your pipeline
Bitbucket Pipelines supports one SSH key per repository. However, you can use multiple keys with a pipeline by adding them as secured variables, and referencing them in the bitbucket-pipelines.yml file.