Troubleshooting webhook security issues
Setting the webhook secret token failed for one or more repositories
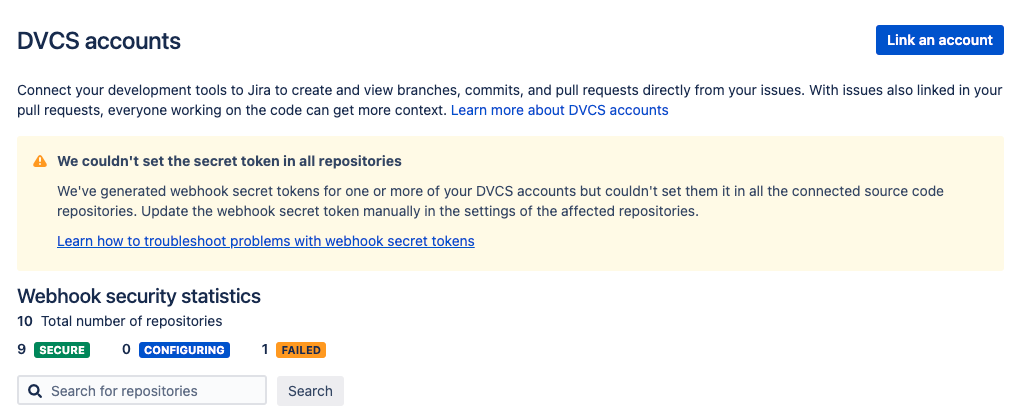
Jira may be unable to update the configuration settings of all repositories in one or more of your DVCS accounts with a newly generated webhook secret token. This problem may occur when configuring the webhook secret token for a linked DVCS account for the first time or after requesting its regeneration.
Symptoms
If the problem occurs, the affected DVCS accounts and repositories will be marked with the FAILED webhook security status indicator. Jira will also notify you about the problem on the DVCS accounts page with the following warning message:
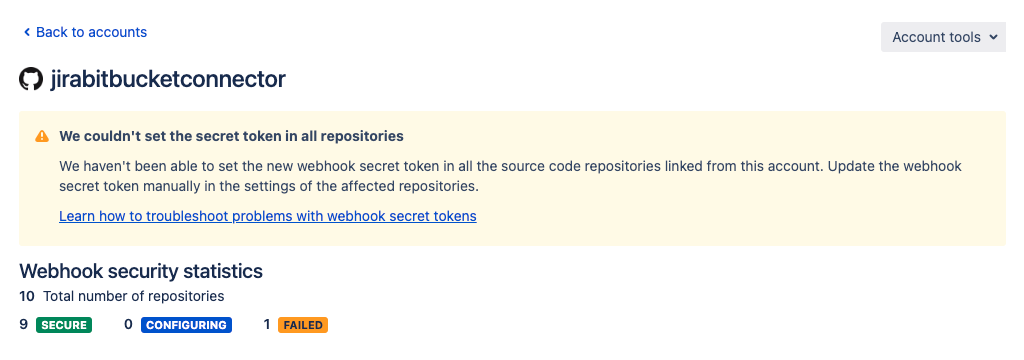
Similarly, the DVCS account details page for the affected DVCS account will display the following warning message:
Resolution
To resolve this issue you can:
- Manually set the webhook secret token in the settings of the affected repositories
- Force Jira to retry setting the webhook secret token in the affected source code repositories
Manually setting the webhook secret token in the affected repositories
Set the webhook secret token in the configuration settings of the affected repositories manually. After a webhook request is received, the webhook security status will change to SECURE.
Learn how to configure a webhook for a project or group in GitLab
Learn how to edit webhooks in GitHub & GitHub Enterprise
Retrying the attempt to set the webhook secret token
You can force Jira to retry setting the webhook secret token in the configuration settings of the affected source code repositories. To do that, manually update the Jira database to reset the webhook security status of the failed repositories back to CONFIGURING as described in one of the following sections:
The database queries included in the following sections were written for PostgreSQL. If you’re using Jira with another database engine, adjust the queries to match the requirements of your database.