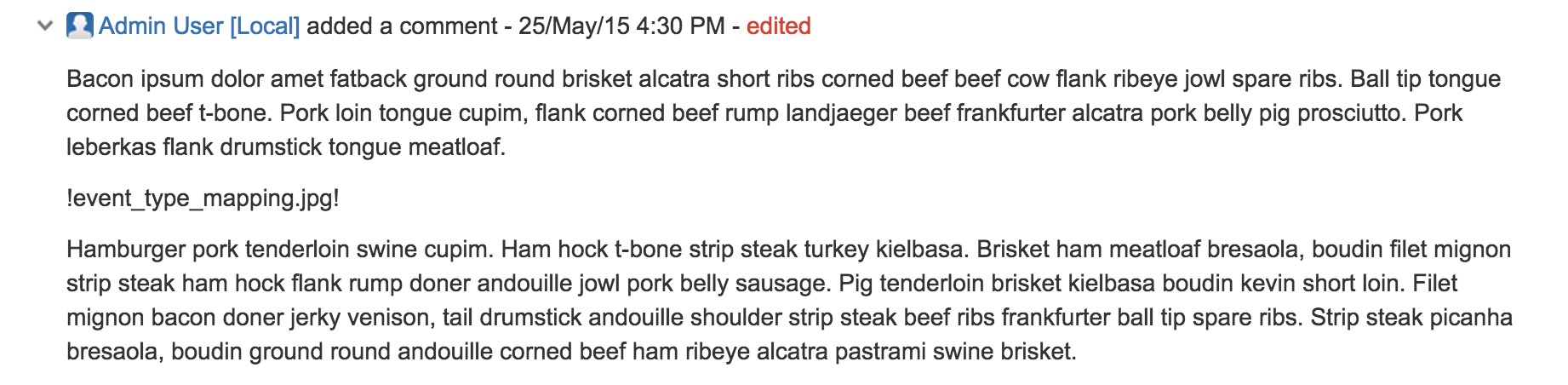
Image attachments are not displayed inline in wiki renderer fields
Platform Notice: Data Center - This article applies to Atlassian products on the Data Center platform.
Note that this knowledge base article was created for the Data Center version of the product. Data Center knowledge base articles for non-Data Center-specific features may also work for Server versions of the product, however they have not been tested. Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
Problem
Image attachments do not display inline in wiki renderer fields when using the wiki markup such as !image.png! in a Jira issue. For example:
Diagnosis
All other wiki markup appear to be working fine e.g. [^image.png]. (But you may also have interference with other wiki markup next to the image.)
Cause
In Jira's General Configurations Settings, the option "Internet Explorer MIME Sniffing Security Hole Workaround Policy" has been set to "Secure: forced download of attachments for all browsers". When set to 'secure' this disables the ability to render any attachments inline without downloading, including images unfortunately. This applies to all browsers.
There was a suggestion raised in JRASERVER-43914 - Remove Internet Explorer MIME Sniffing Security Hole Workaround Policy to remove this as IE7 is no longer supported, but it was deemed to be a still necessary security measure but not directly related to just IE7 anymore. Instead JRASERVER-45348 - Rename the Internet Explorer MIME Sniffing Security Hole Workaround Policywas raised to rename the setting to a more appropriate name.
Workaround
To display inline images in JIRA fields try set the "Internet Explorer MIME Sniffing Security Hole Workaround Policy" option to either "Insecure: inline display of attachments" or "Work around Internet Explorer security hole".
Cloud customers might have to contact the Atlassian Support to have the workaround applied.