HipChat Server Security
This page provides security details and recommendations
SSL encryption
HipChat uses 256-bit SSL encryption to transmit your data and files. This is the same encryption used by online banks and retailers.
Open ports
HipChat Server requires you to have a small set of inbound and outbound TCP ports open. For the list of ports, see the System Requirements for HipChat Server. HipChat Server does have an internal firewall which does basic traffic protection while allowing the required ports.
Recommendations for deploying HipChat Server from an OVA
These recommendations apply to people deploying HipChat Server using the open archive (OVA) image on a virtual machine.
To ensure HipChat Server is configured securely, we recommend you take the following steps:
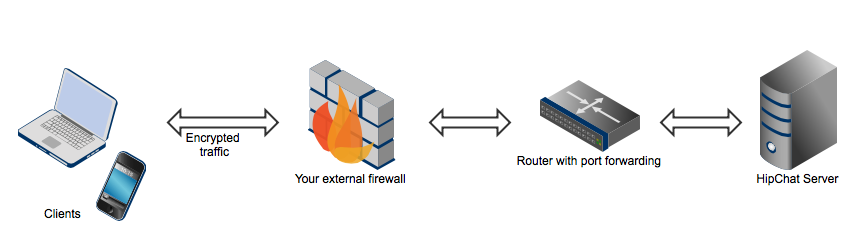
- Add an external firewall as the first point to filter traffic. (For example, you can add additional filters by IP address.)
- Configure a router with port forwarding. (This way, you control the routing table and only forward the required open ports.)
- Change the default console/SSH admin password. For instructions, see Deploying from the OVA image
- Replace the self signed SSL certificate with one from a trusted Root CA vendor. For instructions, see Creating or Obtaining an SSL Key and Certificate.
- Check the list of features and disable any features you're not using:
- Log in to HipChat Server. For example: https://hipchat.fully-qualified-domain-name.com or https://IPv4
- Click Group admin > Features. You can disable some features and restrict others to administrators.
- Click Server admin > Video. You can disable video chat, here.
Note: HipChat Server has an internal firewall that does basic traffic protection while allowing the required ports to be open.
Don't modify HipChat Server's internal firewall. By modifying it, you may inadvertently create a security risk.
Recommendations for deploying HipChat Server using an AMI
If you're deploying HipChat Server using an Amazon Machine Image (AMI), Amazon Web Services have their own additional security infrastructure. You can learn more at Amazon Web Services Security Center.
Deploying HipChat Server in a VPN
You can deploy your HipChat Server behind your firewall with internal-only access rules, an internal IP address, or a private DNS. This will require all inbound client access to be from within your organization's VPN.
You must ensure your HipChat clients can perform DNS resolution to a VPN-deployed HipChat Server.
Note: Many integrations expect direct access to HipChat Server. Check the details of any integration you wish to install.
Deploying HipChat Server in a DMZ
You can deploy HipChat Server in a DMZ, but you must ensure access to any internal systems that your HipChat Server might need. For example if your deployment is using the directory integration, then it would need access to your LDAP server.
Hiding message previews in notifications
If you don't want messages showing up in notifications on mobile devices or in emails, you can disable message previews. You can learn more at Hide message previews on notifications.
