App signing troubleshooting
When dealing with app signing issues, it’s important to follow a systematic approach to identify and resolve the problem. Below are common issues and their solutions.
On this page:
Problem: App signing is preventing app installation or upgrade and is not desired.
Solution: Disable app signing.
In UPM 8.0, the easiest way to disable the feature is to set the atlassian.upm.signature.check.disabledsystem property to true.
You can set this in either of two locations.
JVM option
Open the JVM options for your instance: Setting properties and options
Add this line to the JVM options:
--Datlassian.upm.signature.check.disabled=trueRestart Jira for the new option to take effect.
UPM config option
Add the line atlassian.upm.signature.check.disabled=true to the upmconfig/upm.properties file.
Missing certificates
Problem: The signature verification for Marketplace apps is failing.
Solution: Ensure that the Trust store contains the necessary trusted certificates. UPM lists the Trust store certificates on the Trusted Certificates admin page.
Expired certificates
Problem: The signing certificate will soon expire or has expired. By default, the expiration warning is set to 30 days.
Starting with version 3.1.0, ATST (Atlassian Troubleshooting and Support Tool) introduces a health check that monitors the expiration dates of certificates used by UPM to check app signatures.
You'll receive a warning message if any certificate is about to reach its expiration.
Health check results
| Icon | Result | What this means |
|---|---|---|
| There are no certificates with expiration dates in the next 30 days. | No certificates in UPM’s trust store will expire in the coming 30 days. | |
| There are certificates that need attention as they're approaching expiration or have already expired. For more details, see the Trusted Certificates page in the administration console. | If you still need to install apps from the certificate issuer, replace the expiring certificates. Otherwise, remove the expired certificates from the trust store. |
What happens if I ignore the warning?
Once a certificate reaches expiration, UPM will fail to check app signatures using this certificate, and won't install certain apps (Atlassian Marketplace, or apps from a vendor that issued the certificate).
Solution
- Install a recent Atlassian Certificates Bundle. If the expiring certificate was issued by Atlassian and was used to install apps from the Marketplace, follow this documentation: Updating Atlassian Certificates Bundles
- Get a new certificate from a vendor. If the expiring certificate was issued by an app vendor, get a new certificate from the vendor, and install it in the UPM truststore folder as described in Configuring UPM signature check.
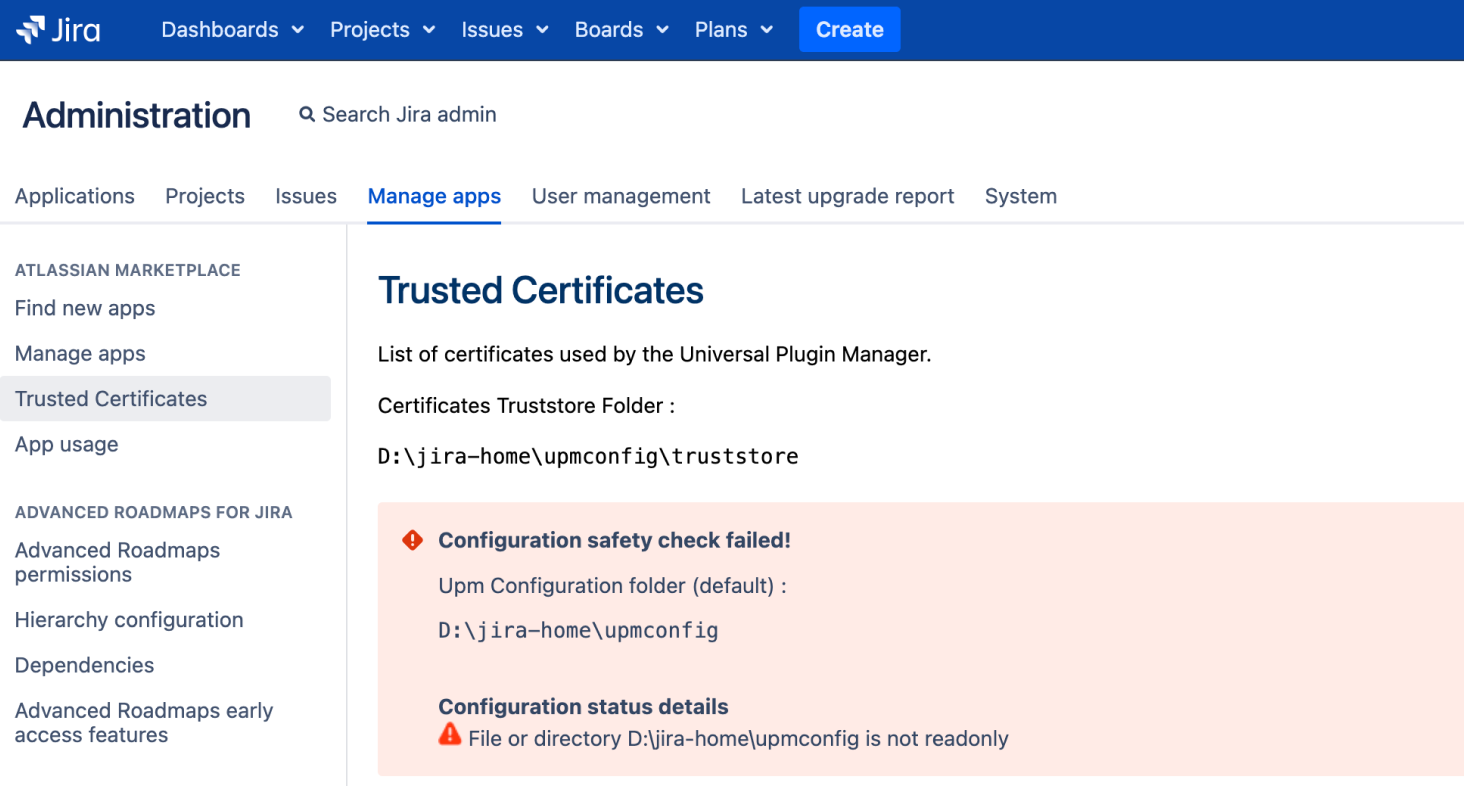
Invalid trust store permissions
Problem: The upmconfig folder has been set up with incorrect permissions.
Error on the Trusted Certificates page
The following are examples of errors you might receive on the Trusted Certificates page under Manage apps:
- The “File or directory is not read-only” error appears when a file or directory is writable by the user running the application.
- The “File or directory belongs to the current user” error appears when an element of the configuration folder belongs to the user running the application.
Error in ATST app
Starting with version 3.1.0, ATST (Atlassian Troubleshooting and Support Tool) introduces a health check that monitors the status of UPM’s configuration and certificate files used to check for app signatures. You'll receive a warning message if any file used by this feature isn't compliant with the following rules:
- the file is writable by the user running the Data Center app
- the file belongs to the user running the Data Center app
| Icon | Result | What this means |
|---|---|---|
| The truststore folder configuration is valid. | The configuration is safe. | |
| The truststore folder configuration needs attention. For more details, see the Trusted Certificates page in the administration console. | Some files aren't compliant with the rules. The Trusted Certificates page displays a list of all non-compliant files, each with a mention of the non-compliance. |
What happens if I ignore the warning?
UPM won't be able to check app signatures and will prevent app installation.
Solution
Depending on the broken rule, two actions can solve this problem:
- Change the file ownership. If one or more files belong to the user running the Data Center app, you'll need to have filesystem access and privileges to change the ownership of the files to another user, making sure the user running the Data Center app can still read them.
- Change the file permissions. If one or more files are writable by the user running the Data Center app, you'll need to have file system access and privileges to remove the write privileges of the files from the user running the Data Center app.
For further guidance, check UPM documentation: Configuring UPM app signature check.
Signature mismatch
Problem: The app signature does not match the expected signature.
Solution: Verify the signature using openssl.
# Extract public key from PEM certificate
openssl x509 -in certificate.crt -noout -pubkey > public_key.pem
# Verify Base64 encoded signature
openssl pkeyutl -verify -pubin -inkey public_key.pem -rawin -in app.jar -sigfile signature.txt.sigNote that Base64 encoded signatures and certificates must be decoded first using:
base64 --decode -i base64.txt -o decoded_outputAdditional tips
- Backup your Trust store: Ensure that you maintain a backup of your Trust store in a secure location.
- Documentation: Check the official documentation for guidance on signing your custom apps.
- Continuous Review: Regularly assess and delete unused or unnecessary certificates from your Trust Store.