SSH access keys for system use
- ED25519
- RSA2
- ECDSA
- DSA (we recommend you use other key types)
- ED25519-SK
- ECDSA-SK
Although Bitbucket supports the above key types, your admin can restrict specific key types and mandate minimum key lengths to make sure you’re using secure SSH keys. Learn more about how your admin can manage settings for SSH keys
Before you can use SSH keys to secure a connection with Bitbucket the following must have already been done:
- Your Bitbucket administrator must have already enabled SSH access, on Bitbucket.
- Your Bitbucket administrator must already have enabled the option SSH access keys enabled on Bitbucket.
- You must have already created an SSL key. See Creating SSH keys. Alternatively, you can use an existing key, if it isn't already being used for a personal account in Bitbucket.
Using SSH keys to allow access to Bitbucket repositories
To get the SSH key to work with your build, or other, system, you need to:
- Add the private key to that system. For Bamboo, see this page: Shared credentials.
- Add the public key to Bitbucket as described below.
Add an SSH access key to either a Bitbucket project or repository
You simply copy the public key, from the system for which you want to allow access, and paste it into Bitbucket.
Copy the public key. One approach is to display the key on-screen using
cat, and copy it from there:cat < ~/.ssh/id_ed25519.pubNow, in Bitbucket, go to the Settings tab for the project or repository.
Click Access keys and then Add key.
- Paste the key into the text box.
- (Optional) Name your key to identify it easily.
- Choose the Read permission, for
git pullorgit cloneoperations for example, where you want to be sure that the system will not be able to write back to the Bitbucket repository.
Choose the Read / Write permission, forgit pushorgit mergeoperations for example, where you may want your build system to merge successful feature branch builds to the default branch in the Bitbucket repository, or so that deployments can be tagged.
Note that if you attempt to add a key already present on a project or repository but with a different permission to what it currently has, the permission and label will simply be updated. - (Optional) Set an expiry so your key expires automatically.
If your admin has set automatic expiry for all keys across Bitbucket, the key expires based on the limits they've set. If required, you can set the key to expire earlier than the limit they've set.
Note that you can't edit the expiry after you create the key. Click Add key.
Bitbucket license implications
- System access keys do not require an additional Bitbucket user license.
Reusing access keys
- You can use the same SSH access key for multiple repositories or projects.
- Keys used for personal user accounts can't be re-used as a project or repository system access key, and keys used as a project or repository access key can't be re-used for user accounts.
Deleting an access key
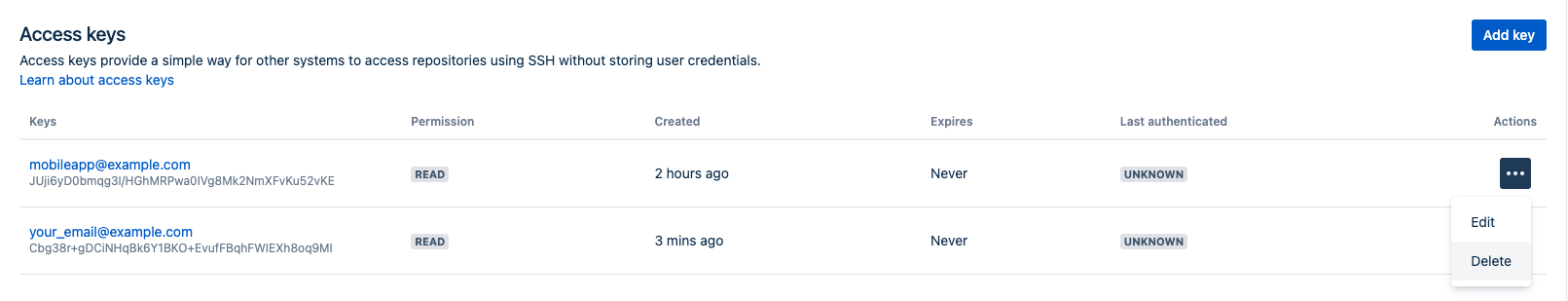
To delete an access key:
- Navigate to Repository Settings or Project Settings > Access keys.
- Select More actions > Delete.
If the key is used for multiple projects or repositories, you can select the other places that you want the key to be deleted from:
Note that the dialog only displays the projects and repositories that you have permission to see. Be aware that the key may also be used in other places that are not listed in the dialog. To be 100% sure that all uses of the key are deleted, this operation must be performed by someone with the administrator or sysadmin global permission .